Enhanced Zeus Sphinx Trojan Used in COVID-19 Schemes
Data Breach Today
MAY 12, 2020
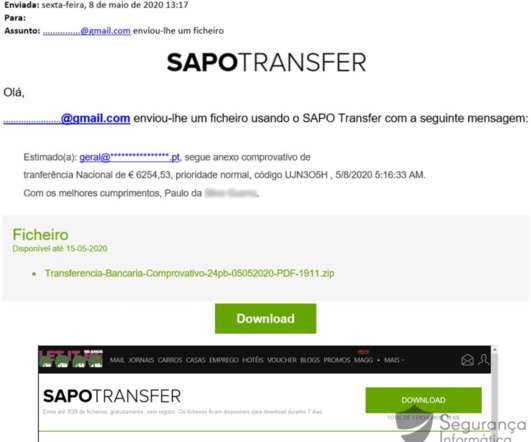
Researchers Say New Features and Functionality Added The operators behind the Zeus Sphinx malware have added new features and functionality to the Trojan, and more cybercriminals have deployed it within phishing campaigns that use the COVID-19 crisis as a lure, according to IBM X-Force. The Trojan has become more efficient at stealing banking data.









































Let's personalize your content