Microsoft, Others Dismantle Trickbot Botnet
Data Breach Today
OCTOBER 12, 2020
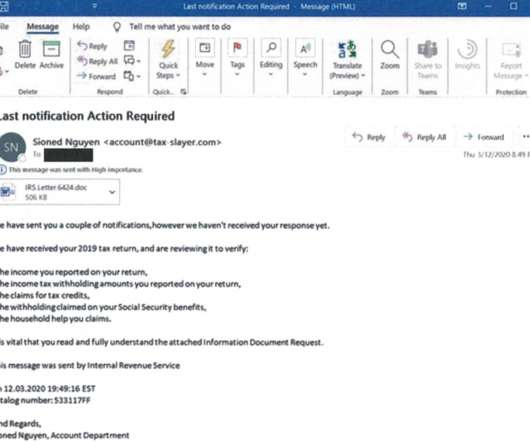
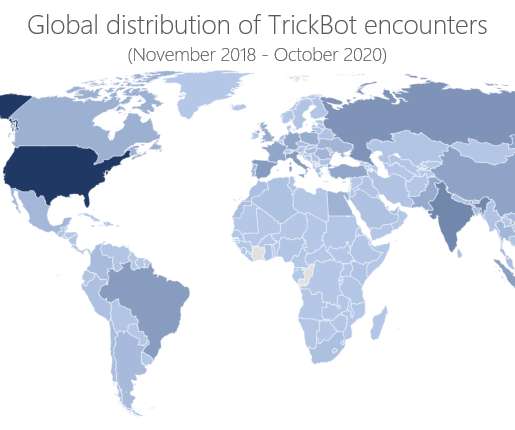
Court Order Enables Takedown of Servers to Disrupt Malware, Protect Election Microsoft collaborated with cybersecurity companies and government agencies to take down the million-device Trickbot botnet in an effort to help protect the Nov. 3 U.S. election and stop the global spread of ransomware and other malware.







































Let's personalize your content