Anatomy of a Breach: Criminal Data Brokers Hit Dave
Data Breach Today
JULY 28, 2020
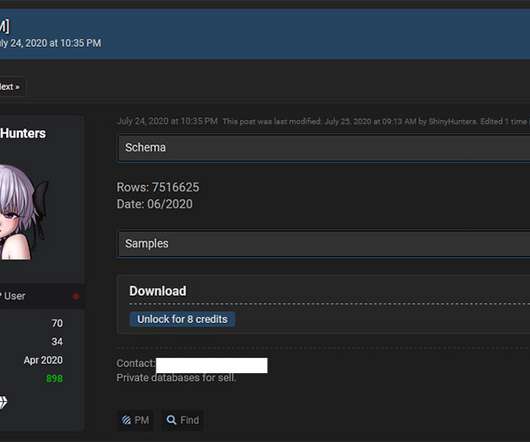
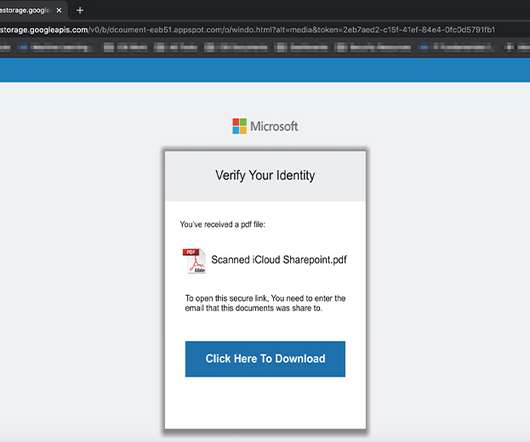
Evidence Points to 'ShinyHunters' Hacking Team Phishing Employees of Mobile Bank Mobile banking startup Dave is just the latest victim of criminal data brokers. Extensive evidence now points to Dave having been hit by a ShinyHunters, which has been tied to the sale of millions of stolen records to fraudsters - either via a phishing attack or hack of a third-party service provider.




































Let's personalize your content