Ontario Teachers’ Data Stolen in Ransomware Attack
Data Breach Today
NOVEMBER 25, 2022
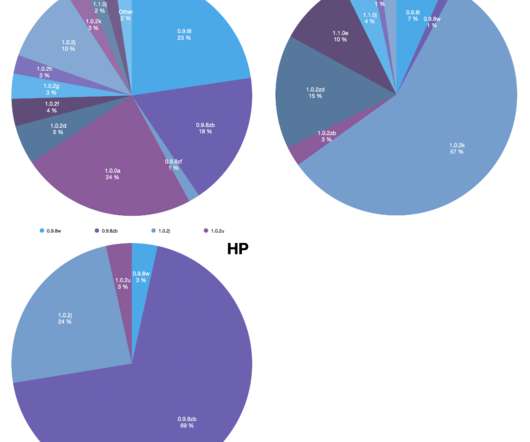
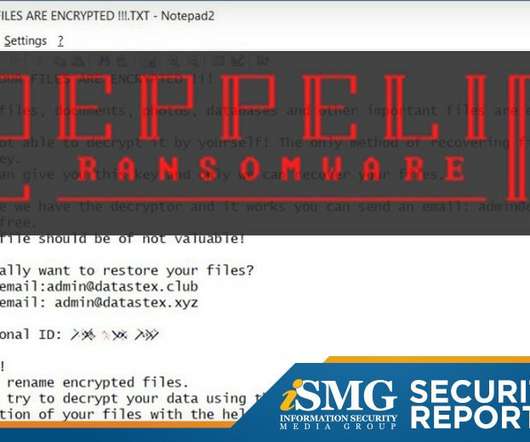
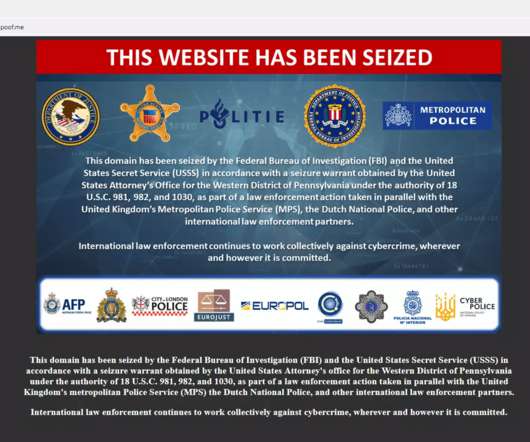
Victims Notified of Ransomware Attack Six Months After the Incident A cyberattack on a Canadian teachers’ union gave thieves access to sensitive data of more than 60,000 members The union is yet to disclose the exact number of affected individuals, but stated that both former and current members are impacted.























Let's personalize your content