Getting Ahead of Supply Chain Attacks
Dark Reading
JULY 25, 2022
Attackers are willing to replicate entire networks, purchase domains, and persist for months, not to mention spend significantly to make these campaigns successful.

Dark Reading
JULY 25, 2022
Attackers are willing to replicate entire networks, purchase domains, and persist for months, not to mention spend significantly to make these campaigns successful.

Data Breach Today
JULY 25, 2022
Directive Emphasizes Continuous Monitoring and Assessments U.S. federal regulators are revamping their approach to oil pipeline cybersecurity by telling operators they have newfound latitude so long as they implement continuous monitoring and test their posture. Pipeline cybersecurity became a priority after a 2021 ransomware attack led to gas shortages.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
JULY 25, 2022
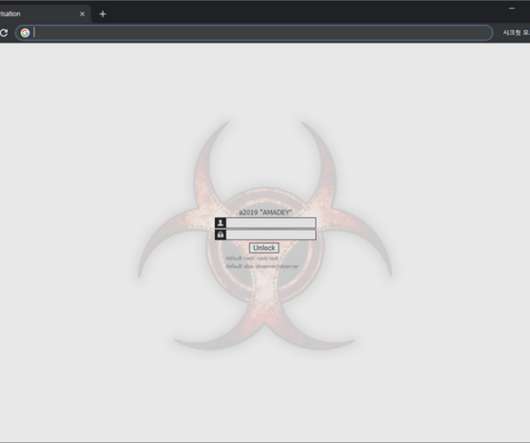
Operators behind the Amadey Bot malware use the SmokeLoader to distribute a new variant via software cracks and keygen sites. Amadey Bot is a data-stealing malware that was first spotted in 2018, it also allows operators to install additional payloads. The malware is available for sale in illegal forums, in the past, it was used by cybercrime gangs like TA505 to install GandCrab ransomware or the FlawedAmmyy RAT.

Data Breach Today
JULY 25, 2022
Hackers Stole Sensitive Data for 57 Million Uber Passengers and Drivers Ride-sharing service Uber has reached an agreement with the U.S. Department of Justice to resolve a criminal investigation into its massive 2016 data breach. After Uber admitting to covering up the data breach, as well as several other factors, the government has ended its prosecution.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Security Affairs
JULY 25, 2022
Drupal development team released security updates to fix multiple issues, including a critical code execution flaw. Drupal developers have released security updates to address multiple vulnerabilities in the popular CMS: Drupal core – Moderately critical – Multiple vulnerabilities – SA-CORE-2022-015 Drupal core – Critical – Arbitrary PHP code execution – SA-CORE-2022-014 Drupal core – Moderately critical – Access Bypass – SA-CORE-2022-013 Dru
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

KnowBe4
JULY 25, 2022
The Colonial Pipeline ransomware attack of 2021 put infrastructure operators on notice that they were directly in the crosshairs of big ransomware gangs. The reaction of law enforcement seems, however, to have also put the gangs on notice that their ability to operate with impunity isn’t what it used to be. The big criminal operations seem to be breaking up.

Data Breach Today
JULY 25, 2022
Protocol's Governance Contract, Vulnerable for 2 Years, Exploited in Attack A music streaming blockchain service patched a bug on a smart contract that went undetected since 2020. An attacker used it to steal $AUDIO crypto tokens worth nearly $6 million, selling them for more than $1 million. The vulnerability wasn't detected by multiple smart contracts security audits.

Security Affairs
JULY 25, 2022
The ransomware group Lockbit claims to have stolen 78 GB of files from the Italian Revenue Agency (Agenzia delle Entrate). The ransomware gang Lockbit claims to have hacked the Italian Revenue Agency (Agenzia delle Entrate) and added the government agency to the list of victims reported on its dark web leak site. “The Revenue Agency, operational since 1 January 2001, was born from the reorganization of the Financial Administration following the Legislative Decree No. 300 of 1999.

Data Breach Today
JULY 25, 2022
Security Director Ian Keller Tells You How to Become Enabled to Fix What's Broken Getting cybersecurity right means CISOs need peer relationships with other operations executives. CISOs need board access and a handle on the company business, writes Ian Keller, director of security at a telecom company. "And then you'll wake up and realize this is not as simple as it sounds.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Dark Reading
JULY 25, 2022
In the latest iteration, Qakbot operators are using DLL sideloading to deliver malware, a technique that places legitimate and malicious files together in a common directory to avoid detection.

Data Breach Today
JULY 25, 2022
Growth at All Costs Is So 2021 - Now It's All About Taking a Path to Profitability Nascent startups have ditched the "growth at all costs" mantra of 2021 to hold onto enough cash to weather the macroeconomic storm expected later this year. Gone are the days of security vendors promising to double annual sales while burning cash even faster than they bring in new business.

Dark Reading
JULY 25, 2022
Two previously unknown critical vulnerabilities within FileWave’s multiplatform MDM system could grant malicious actors access to the platform's most privileged user account.

Data Breach Today
JULY 25, 2022
Latest Targets: Ukraine's Largest Radio Broadcaster, Government Software Provider Ukrainian network defenders continue to contend with a barrage of malware attacks. Apparent Russia hackers broadcast disinformation about Ukrainian President Volodymyr Zelenskyy's health and targeted a software developer with government customers.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

DLA Piper Privacy Matters
JULY 25, 2022
Authors: Sarah Birkett and Alex Moore . The use of CCTV systems to collect biometric information from individuals in Australia is attracting headlines. The issue relates not to the use of CCTV itself, but rather the collection of biometric information (i.e. electronic copies of faces, fingerprints, voices) via CCTV. Organisations, including retailers, may collect biometric information via CCTV for a variety of reasons, including to build profiles of the individuals entering their stores, ident
Security Affairs
JULY 25, 2022
Kaspersky uncovered a new UEFI firmware rootkit, tracked as CosmicStrand, which it attributes to an unknown Chinese-speaking threat actor. Researchers from Kaspersky have spotted a UEFI firmware rootkit, named CosmicStrand, which has been attributed to an unknown Chinese-speaking threat actor. This malware was first spotted by Chinese firm Qihoo360 in 2017.

Dark Reading
JULY 25, 2022
The firmware threat offers ultimate stealth and persistence -- and may be distributed via tainted firmware components in a supply-chain play, researchers theorize.

Security Affairs
JULY 25, 2022
Multiple flaws in FileWave mobile device management (MDM) product exposed organizations to cyberattacks. Claroty researchers discovered two vulnerabilities in the FileWave MDM product that exposed more than one thousand organizations to cyber attacks. FIleWave MDM is used by organizations to view and manage device configurations, locations, security settings, and other device data.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

WIRED Threat Level
JULY 25, 2022
Despite the DOJ vowing to protect people's ability to travel out of state for abortion care, legal experts warn not to take that freedom for granted.
Dark Reading
JULY 25, 2022
After leaking 80 million US customer data records in a cyberattack last summer, T-Mobile offers to settle a wide-ranging class action suit for just $350 million.

KnowBe4
JULY 25, 2022
Just when you thought scammers couldn't get more tricky in their attacks, this example will prove you wrong.

IG Guru
JULY 25, 2022
Active CRMs in good standing are invited to apply for candidacy to a Board of Regents position. CRAs are not eligible to serve on the Board Regents. For more information on terms and time commitment, please click here. President-Elect/Treasurer (2023-2025) The President-Elect/Treasurer is a member of the Executive Committee and serves as custodian of funds, securities, […].

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
WIRED Threat Level
JULY 25, 2022
Since Vladimir Putin blocked Facebook, Instagram, and Twitter in March, Russia has been pushing away from the global internet at a rapid pace.

IG Guru
JULY 25, 2022
PNM Resources is looking for a qualified candidate to fill a Records Compliance Analyst position. This job is based in NM and relocation expenses may be negotiable. Great work environment and fantastic team. Please share widely. To learn more about the company, [link] Thank you, Mary Beth Hames * Records Compliance Analyst / Sr POSTING DEADLINE […].

Dark Reading
JULY 25, 2022
To help discern legitimate traffic from fraud, it helps to understand user intent as shown through their behavior.

Threatpost
JULY 25, 2022
SecuriThings' CEO Roy Dagan tackles the sometimes overlooked security step of physical security maintenance and breaks down why it is important.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
JULY 25, 2022
Several threat actors used Amadey Bot previously to steal information and distribute malware such as the GandCrab ransomware and the FlawedAmmy RAT.

Docuware
JULY 25, 2022
Take a moment to think: At the start of the Covid-19 pandemic, suddenly most of your employees were working remotely. Are the decisions you made under tremendous time pressure within the past 24 months helping or hindering productivity today? Or are you struggling with a makeshift solution you put in place just to get by? Now that you have time to breathe, do you know if you have the right tools to support your hybrid workforce into the future?

Dark Reading
JULY 25, 2022
Security professionals can now achieve real-time protection for their workloads in minutes.
Let's personalize your content