After Joker’s Stash Closes, What Comes Next?
Data Breach Today
FEBRUARY 1, 2021
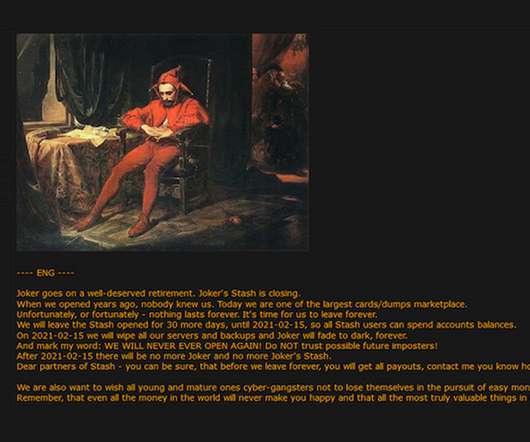
Researchers Expect Other Underground Sites Will Pick Up the Slack Other darknet marketplaces apparently are preparing to fill the underground economy's need for a steady stream of stolen payment card data if the Joker's Stash site closes Feb. 15 as its administrator has announced. Some researchers believe the administrator may even launch a new marketplace.




































Let's personalize your content