10 Ransomware Strains Being Used in Advanced Attacks
Data Breach Today
APRIL 29, 2020
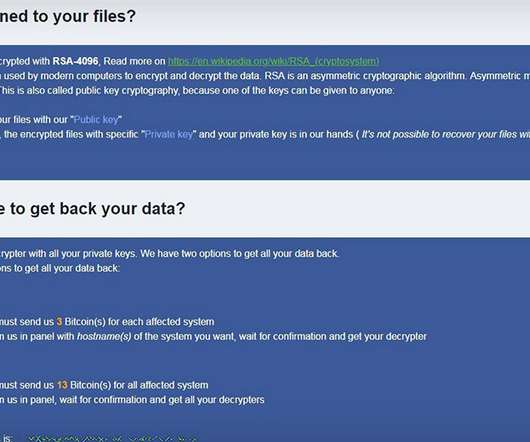
Advanced Hackers Continue to Linger in Breached Networks for Weeks or Months Many attackers continue to camp out in networks for months, conducting reconnaissance and stealing sensitive data before unleashing ransomware. Experts say many recent efforts trace to gangs wielding the RobbinHood, Valet Loader, NetWalker, PonyFinal, Maze and Sodinokibi strains of crypto-locking malware.








































Let's personalize your content