To Survive a Data Breach, Create a Response Playbook
Data Breach Today
DECEMBER 2, 2019
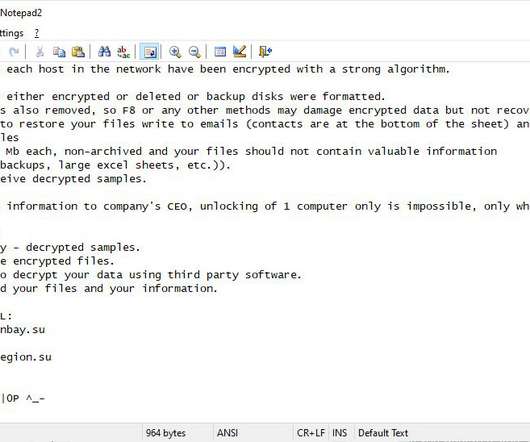
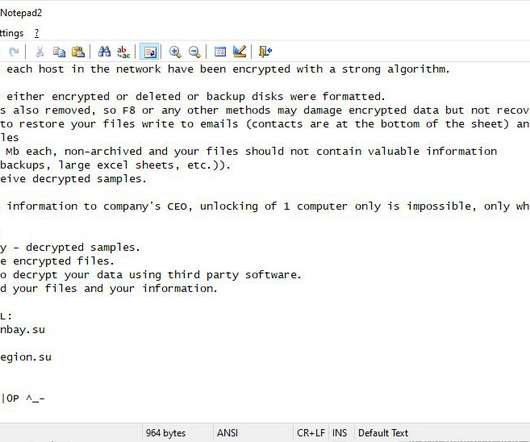
Experts Detail Essential Systems and Procedures Every Organization Needs Now Surviving a data breach requires having a plan, and experts say such plans must be continually tested, practiced and refined. Experts detail seven essential components for building an effective data breach response playbook.



































Let's personalize your content