Hybrid Cloud Changes the Game for Security
Data Breach Today
SEPTEMBER 20, 2022
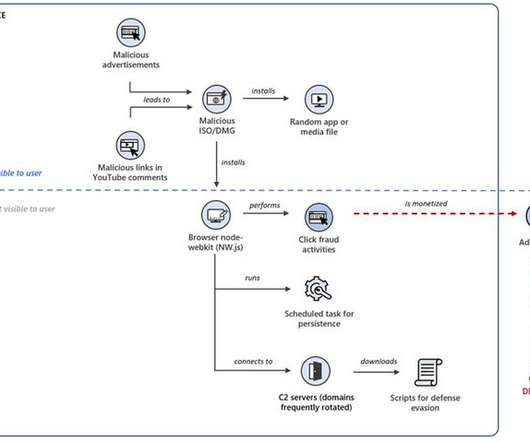
Embracing New Technologies to Gain Agility, Rapid App Delivery Is Good Business Embracing new technologies to gain benefits such as increased agility and rapid application delivery makes good business sense, but existing architectures also need to be maintained and secured to protect the critically important data residing on server workloads across the hybrid cloud.









































Let's personalize your content