The Business of Ransomware: Specialists Help Boost Profits
Data Breach Today
JULY 9, 2021
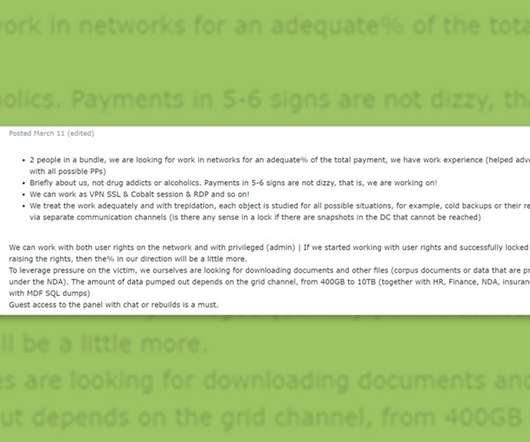
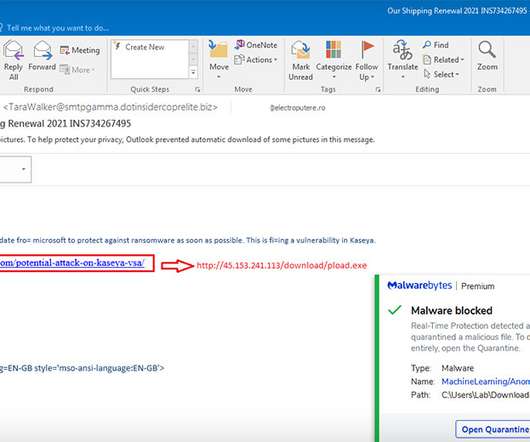
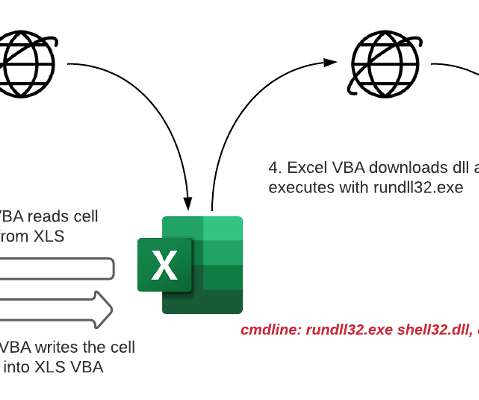
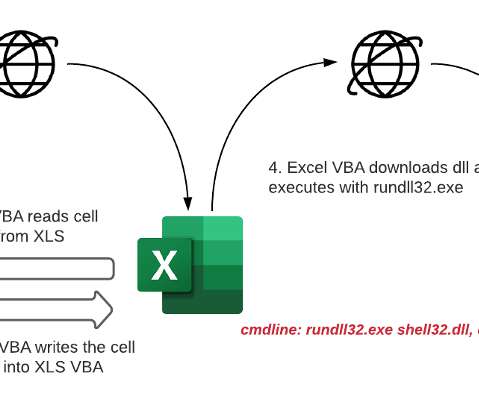
Ransomware-as-a-Service Operations Tap Expert Intrusion Specialists and Negotiators As ransomware attacks become more prolific, their success is being driven by the increasing use of specialists who can refine every stage of an attack. It's a reminder that the goal of cybercrime remains to maximize illicit profits as easily and quickly as possible.





































Let's personalize your content