StrRAT Masquerades as Ransomware
Data Breach Today
MAY 24, 2021
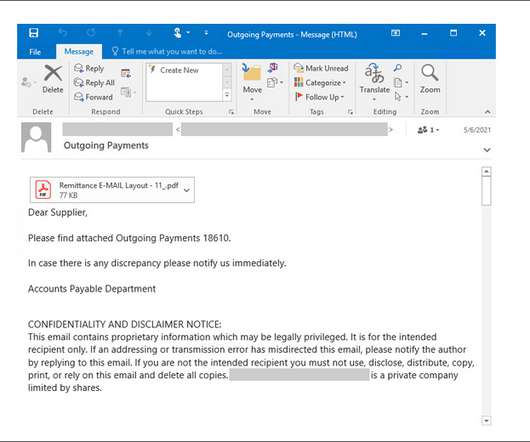
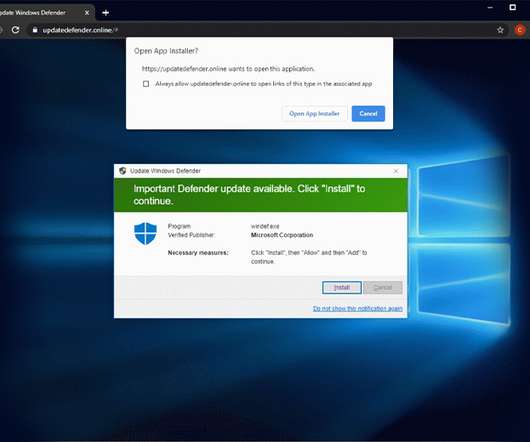
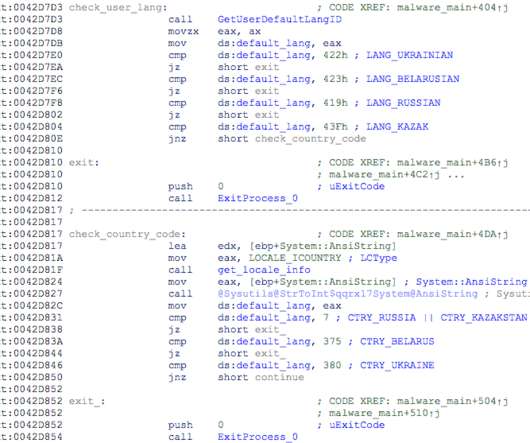
Microsoft Says Spam Campaign Uses Updated Variant Microsoft is warning about a spam campaign that uses an updated variant of Java-based StrRAT malware that steals confidential data while disguising itself as a ransomware infection even though it does not actually encrypt data.




































Let's personalize your content