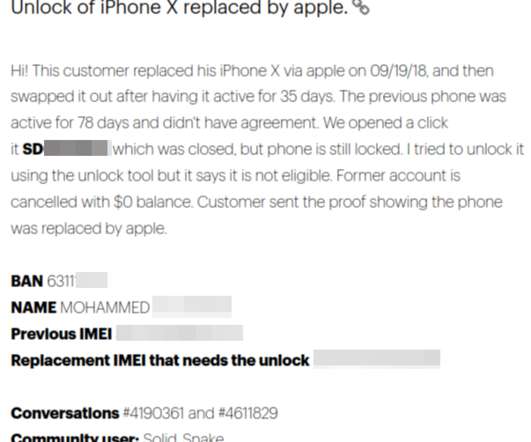
Wawa's Stolen Payment Cards Are Now for Sale
Data Breach Today
JANUARY 29, 2020
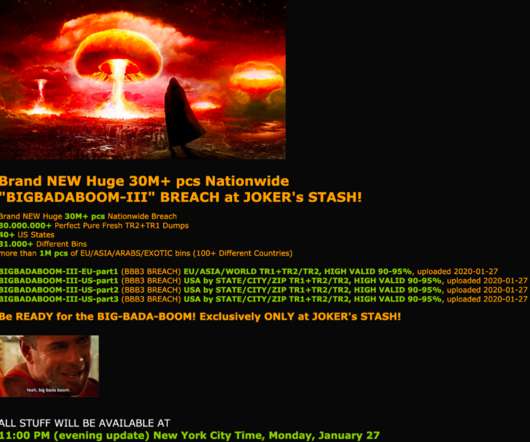
Fraud Marketplace Joker's Stash Says it Has 30 Million Cards A long-running marketplace for selling stolen payment card data claims it has 30 million stolen payment cards that experts believe are linked to the breach at Wawa convenience stores late last year. The breach is one of the largest ever involving card-related data.






































Let's personalize your content