New Entrants to Ransomware Unleash Frankenstein Malware
Data Breach Today
JUNE 9, 2023
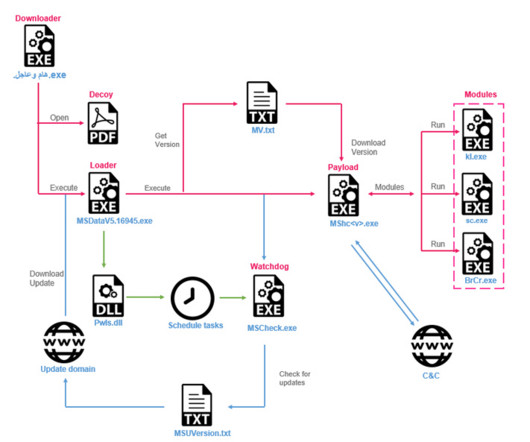
Opportunistic, Less Sophisticated Hackers Test Limits of the Concept of Code Reuse Ransomware hackers are stretching the concept of code reuse to the limit as they confront the specter of diminishing returns for extortionate malware. In their haste to make money, some new players are picking over the discarded remnants of previous ransomware groups.









































Let's personalize your content