The Global Threat Landscape 1 Year After SolarWinds
Data Breach Today
APRIL 25, 2022
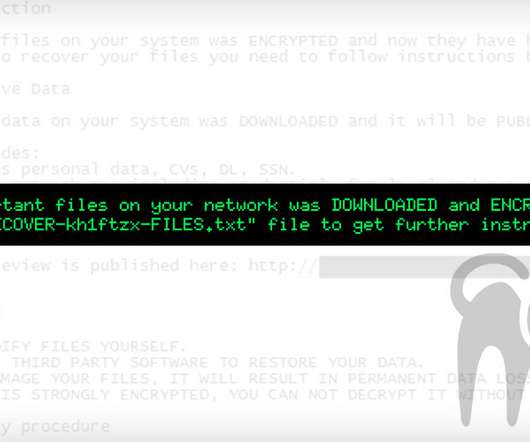
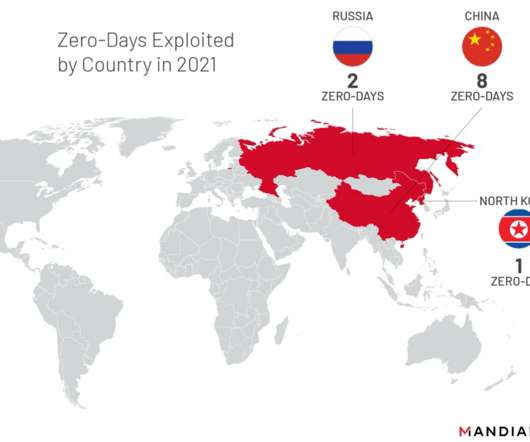
In this episode of "Cybersecurity Unplugged," Roger Sels, vice president, solution, EMEA at BlackBerry, discusses the global threat landscape one year after SolarWinds, including cyberthreats from Russia and China; the cyber impact of the Russia-Ukraine war; and the cyber call to action.






































Let's personalize your content