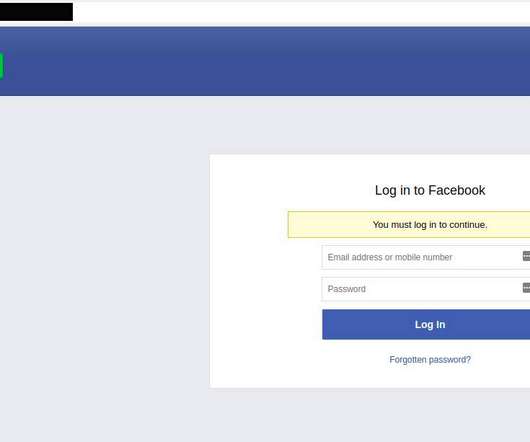
Facebook ads used to steal 615000+ credentials in a phishing campaign
Security Affairs
JANUARY 1, 2021
Cybercriminals are abusing Facebook ads in a large-scale phishing scam aimed at stealing victims’ login credentials. Researchers from security firm ThreatNix spotted a new large-scale campaign abusing Facebook ads. Threat actors are using Facebook ads to redirect users to Github accounts hosting phishing pages used to steal victims’ login credentials.


















Let's personalize your content