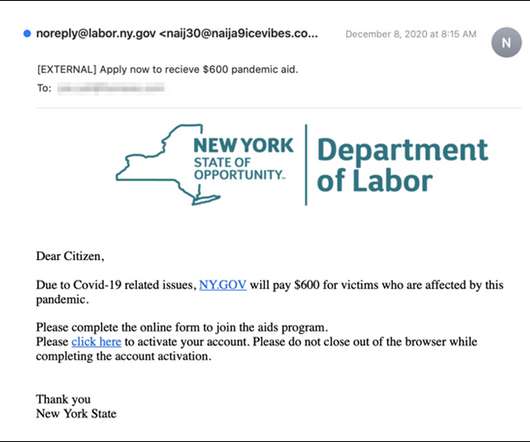
Ex-NSA Director: SolarWinds Breach Is 'A Call for Action'
Data Breach Today
DECEMBER 23, 2020
Ret. Gen. Keith Alexander on How Public and Private Sectors Must Respond He has commanded armed forces and directed the NSA. Now, he's president of vendor IronNet Cybersecurity. From this unique perspective, retired General Keith Alexander says the SolarWinds breach is "a call for action.






































Let's personalize your content