Google Play Source Code Flaw Makes Apps Vulnerable
Data Breach Today
DECEMBER 5, 2020
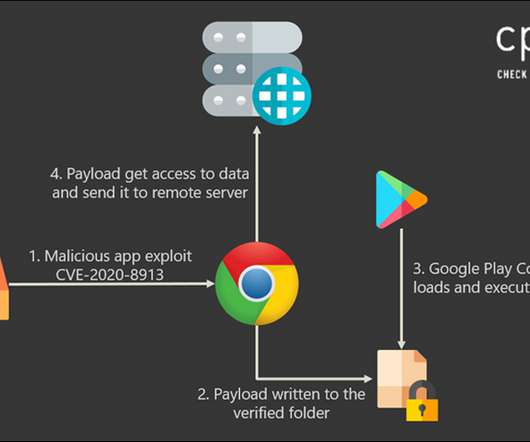
Check Point: Apps Vulnerable to a Source Code Flaw in Google Play A source code flaw in the Google Play store platform could enable attackers to perform remote code execution for credential theft on several prominent apps, a new report by security firm Check Point Research finds.












Let's personalize your content