Morgan Stanley Hit With $5 Million Data Breach Suit
Data Breach Today
SEPTEMBER 1, 2020
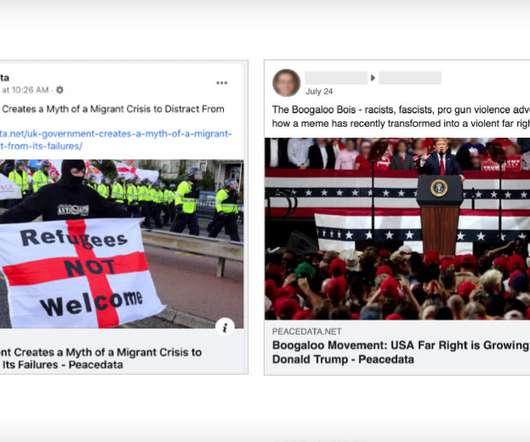
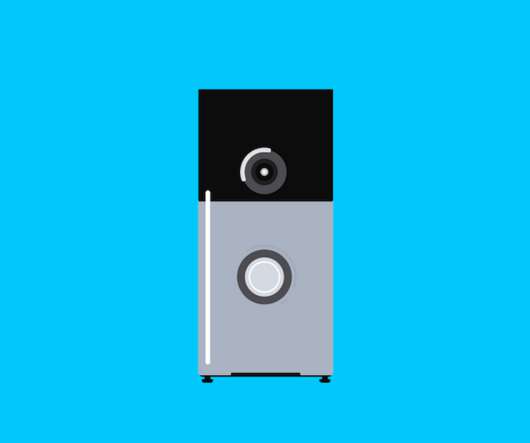
Poor Procedures for Discarding Old Equipment Led to Breach, Lawsuit Alleges A $5 million lawsuit seeking class action status has been filed against Morgan Stanley, claiming the financial organization failed to properly safeguard personally identifiable information when the company discarded old computer equipment.








































Let's personalize your content