Microsoft Warns of COVID-19 Phishing Emails Spreading RAT
Data Breach Today
MAY 22, 2020
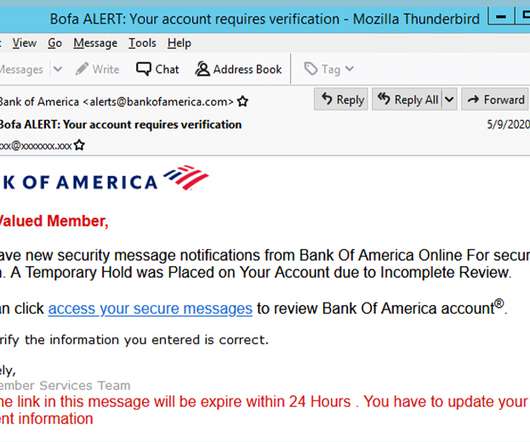
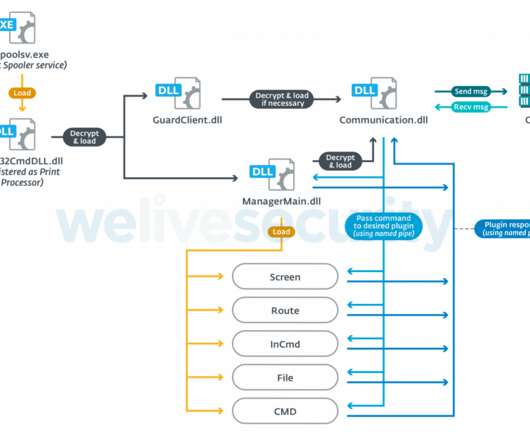
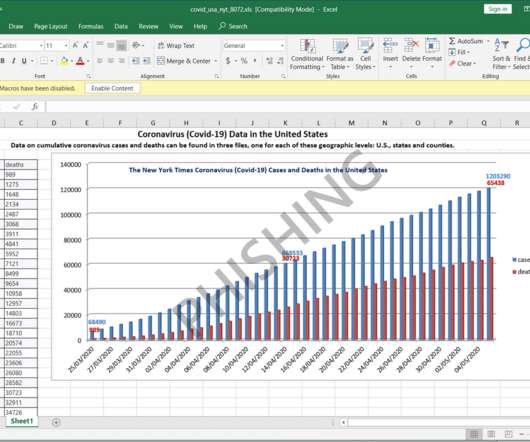
Malicious Messages Attempt to Install NetSupport Manager Tool on Devices Microsoft is warning Windows users about an ongoing "massive" COVID-19-themed phishing campaign that is attempting to install the NetSupport Manager on devices. Attackers can turn NetSupport into a remote access Trojan, or RAT.





































Let's personalize your content