Experts warn of ransomware attacks against government organizations of small states
Security Affairs
MAY 31, 2022
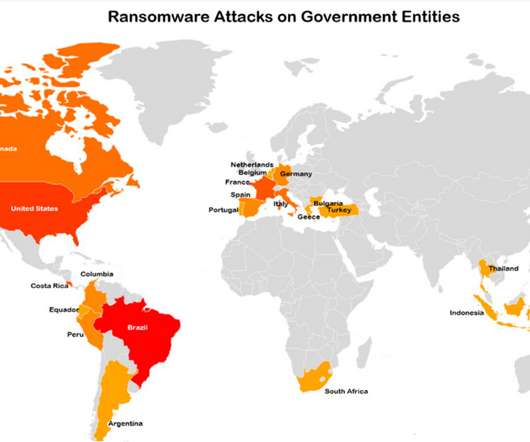
Cyber Research Labs reported a rise in ransomware attacks in the second quarter of 2022, small states are more exposed to these attacks. Cyber Research Labs observed a rise in ransomware attacks in the second quarter of 2022, some of them with a severe impact on the victims, such as the attack that hit the Costa Rican government that caused a nationwide crisis.




































Let's personalize your content