FIN7 Sets Up Fake Pentesting Company Site to Recruit Talent
Data Breach Today
OCTOBER 22, 2021
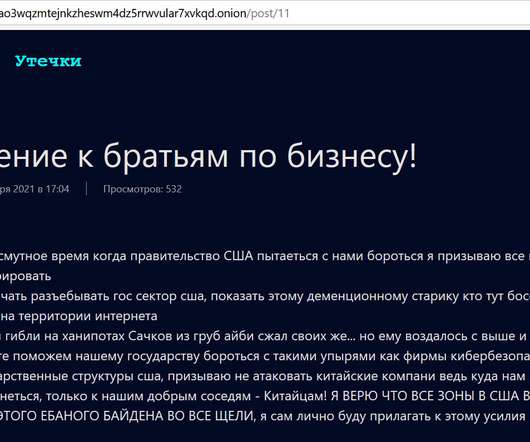
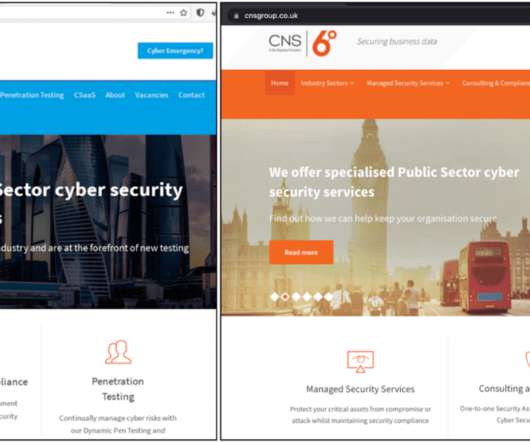
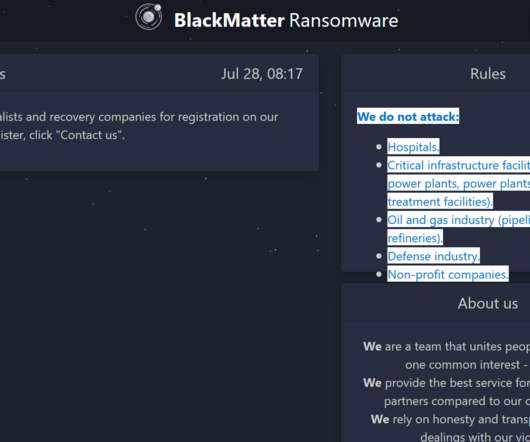
The Cybercrime Group Posted Job Advertisements on Russian Job Portals Threat group FIN7 has set up a website posing as a security company to recruit talent, according to fraud intelligence company Gemini Advisory. The aim of the scam was to lure security researchers who could help the group with penetration testing-related activities to enable ransomware attacks.





































Let's personalize your content