Records Management – the key to information compliance
OpenText Information Management
SEPTEMBER 28, 2020
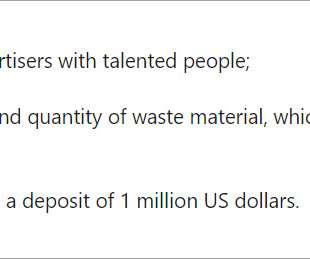
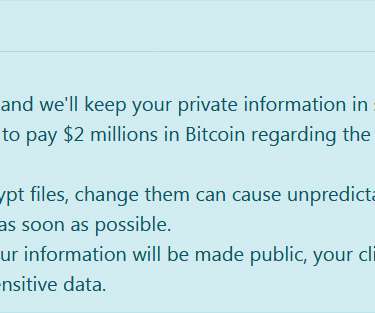
Typically, an organization’s EIM project focuses on Enterprise Content Management (ECM) implementation topics like metadata, folder structures, workflows, system integration and, increasingly, AI support. However, when it comes to Records Management, the discussion often ends with a “we will cover this in a next project phase” approach. This procrastination can pose reputational and financial risk … The post Records Management – the key to information compliance appeared first on Ope




































Let's personalize your content