WSJ: "Cyber Insurance Went Up A Whopping 92% In 2021"
KnowBe4
MAY 18, 2022
Whoa Nellie, that's getting to be real money here. This is the kind of thing that starts cutting into your whole IT budget.

KnowBe4
MAY 18, 2022
Whoa Nellie, that's getting to be real money here. This is the kind of thing that starts cutting into your whole IT budget.
Data Breach Today
MAY 18, 2022
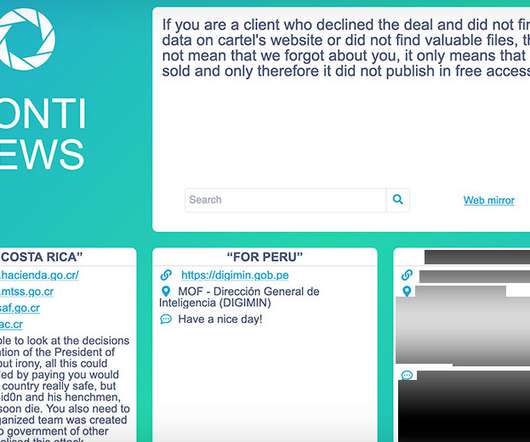
Ransomware Group Continues to Demand Ransom Payment From Besieged Government Ransomware group Conti, which has been holding to ransom crypto-locked Costa Rican government systems since April, has claimed on its leak site Conti News that it has "insiders" in the country's government, and that they are working toward the compromise of "other systems.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MAY 18, 2022
The shift to software-defined everything and reliance on IT infrastructure scattered across the Internet has boosted corporate productivity rather spectacularly. Related: Stopping attack surface expansion. And yet, the modern attack surface continues to expand exponentially, largely unchecked. This dichotomy cannot be tolerated over the long run. Encouragingly, an emerging class of network visibility technology is gaining notable traction.

Data Breach Today
MAY 18, 2022
EDR Deployments Will be Underway at More Than Half of Federal Agencies This Year EDR deployments will be underway at more than half of federal civilian agencies by the end of September, according to federal officials. CISA is currently in the process of deploying EDR across 26 federal civilian agencies and expects to have work underway at 53 agencies by Sept. 30, 2022.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Protection Report
MAY 18, 2022
On May 16, 2022, the Office of the Privacy Commissioner of Canada (the “OPC”) released an Interpretation Bulletin (the “Bulletin”) on what it considers to be “sensitive” personal information under the federal Personal Information Protection and Electronic Documents Act (“PIPEDA”). The Bulletin is meant to act as a consolidated guide based on jurisprudence, regulatory findings, and various interpretations of PIPEDA’s key concepts over the years.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

eSecurity Planet
MAY 18, 2022
Given the insane security environment we are in, it may seem weird to suggest that a tech company is too good at security. How can you be too good at something that is critical to the safety and operational resilience of companies and nations? Security is weird that way. I grew up in the security business – my family owned one of the largest tech security firms when I was a kid.

Data Breach Today
MAY 18, 2022
Scheme Results in Firms Unknowingly Financing Sanctioned Weapons Programs North Korean information technology workers have been attempting to obtain employment in public and private sectors in the United States to fund their home country's weapons of mass destruction and ballistic missiles programs, according to an advisory from U.S. federal agencies.

Schneier on Security
MAY 18, 2022
Researchers have demonstrated iPhone malware that works even when the phone is fully shut down. t turns out that the iPhone’s Bluetooth chip — which is key to making features like Find My work — has no mechanism for digitally signing or even encrypting the firmware it runs. Academics at Germany’s Technical University of Darmstadt figured out how to exploit this lack of hardening to run malicious firmware that allows the attacker to track the phone’s location or run new features whe

Data Breach Today
MAY 18, 2022
More Than 348,000 Patients at Multiple Eye Care Practices Affected So Far The list of ophthalmology practices and the number of individuals affected by a December hacking incident at a cloud-based electronic health records vendor, which resulted in deleted databases, are growing as more details about the attack slowly emerge.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
MAY 18, 2022
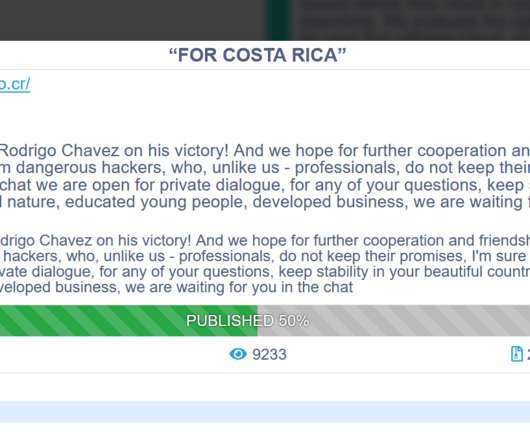
The Conti ransomware gang is threatening to ‘overthrow’ the new government of Costa Rica after last month’s attack. Last month, the Conti ransomware gang claimed responsibility for the attack on Costa Rica government infrastructure after that the government refused to pay a ransom. “The Costa Rican state will not pay anything to these cybercriminals.” said Costa Rica President Carlos Alvarado.

Data Breach Today
MAY 18, 2022
EDR Deployments Will Be Underway at More Than Half of Federal Agencies This Year EDR deployments will be underway at more than half of federal civilian agencies by the end of September, according to federal officials. CISA is currently in the process of deploying EDR across 26 federal civilian agencies and expects to have work underway at 53 agencies by Sept. 30, 2022.

Hanzo Learning Center
MAY 18, 2022
With the ever-increasing growth of enterprise data, meeting compliance guidelines from regulatory bodies regarding digital files, communications, Personal Identifiable Information (PII), financial information, and financial data can be daunting, especially with the increasingly complex and interactive elements common in today’s websites.

Data Breach Today
MAY 18, 2022
Cybersecurity Companies Weigh in on Pros and Cons of the Latest Alert Poor security configurations, weak controls and gaps in authentication protocols are among the common initial access vectors "routinely exploited" by threat actors, the Five Eyes cybersecurity alliance says. Firms offering cybersecurity services weigh in on the gaps and implementation challenges.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

WIRED Threat Level
MAY 18, 2022
To protest the war in Ukraine, WasteRussianTime.today auto-dials Russian government officials, connects them to each other, and lets you listen in to their confusion.

Security Affairs
MAY 18, 2022
Microsoft warns of brute-forcing attacks targeting Microsoft SQL Server (MSSQL) database servers exposed online. Microsoft warns of a new hacking campaign aimed at MSSQL servers, threat actors are launching brute-forcing attacks against poorly protected instances. The attacks are using the legitimate tool sqlps.exe , a sort of SQL Server PowerShell file, as a LOLBin (short for living-off-the-land binary).

Dark Reading
MAY 18, 2022
System of Trust includes data-driven metrics for evaluating the integrity of software, services, and suppliers.

Hunton Privacy
MAY 18, 2022
On May 4-6, 2022, the California Privacy Protection Agency (“CPPA”) held via video conference several public pre-rulemaking stakeholder sessions regarding the California Privacy Rights Act (“CPRA”). During the sessions, stakeholders ranging from privacy and cybersecurity experts to trade associations and California small business owners provided verbal comments, insights and suggestions to the CPPA as it develops the forthcoming CPRA regulations.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Dark Reading
MAY 18, 2022
It has never been more important for organizations of all sizes to prioritize securing their users and their infrastructure secrets with zero-trust network access.
Security Affairs
MAY 18, 2022
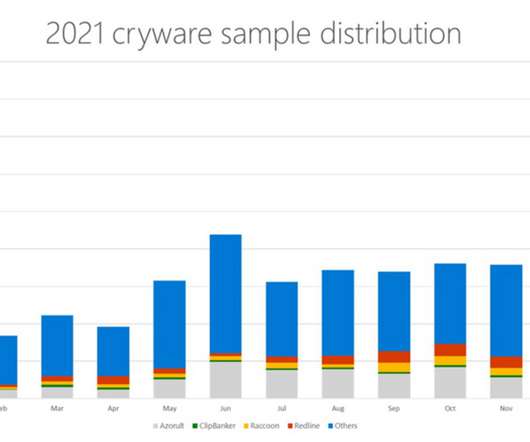
Microsoft researchers warn of the rising threat of cryware targeting non-custodial cryptocurrency wallets, also known as hot wallets. Microsoft warns of the rise of cryware, malicious software used to steal info an dfunds from non-custodial cryptocurrency wallets, also known as hot wallets. Data stolen from this kind of malware includes private keys, seed phrases, and wallet addresses, that could be used by threat actors to initiate fraudulent transactions. “Cryware are information stealer

Dark Reading
MAY 18, 2022
Build security in up front to secure open source code at the foundational level. Apply security controls, have engineering teams test, do code review, and use attacker-centric behavioral analytics to mitigate threats.

Security Affairs
MAY 18, 2022
CISA orders federal agencies to fix VMware CVE-2022-22972 and CVE-2022-22973 vulnerabilities by May 23, 2022. The Cybersecurity and Infrastructure Security Agency (CISA) issued the Emergency Directive 22-03 to order federal agencies to fix VMware CVE-2022-22972 and CVE-2022-22973 flaws or to remove the affected products from their networks by May 23, 2022.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
MAY 18, 2022
From a scrappy contest where hackers tried to win laptops, Pwn2Own has grown into a premier event that has helped normalize bug hunting.

Security Affairs
MAY 18, 2022
VMware addressed a critical authentication bypass vulnerability “affecting local domain users” in multiple products. The virtualization giant warns that a threat actor can exploit the flaw, tracked as CVE-2022-22972 (CVSSv3 base score of 9.8), to obtain admin privileges and urges customers to install patches immediately. “This critical vulnerability should be patched or mitigated immediately per the instructions in VMSA-2021-0014.

Dark Reading
MAY 18, 2022
As demonstrated in Ukraine and elsewhere, the battlefield for today's warriors extends to the virtual realm with cyber warfare.
Security Affairs
MAY 18, 2022
Researchers spotted a new variant of the UpdateAgent macOS malware dropper that was employed in attacks in the wild. Researchers from the Jamf Threat Labs team have uncovered a new variant of the UpdateAgent macOS malware dropper. The new version is written in Swift and relies on the AWS infrastructure to host its malicious payloads. . The new variant of the malware supports common dropper features, including some minor system fingerprinting, endpoint registration, and persistence. “The se

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Dark Reading
MAY 18, 2022
Polygraph Data Platform adds Kubernetes audit log monitoring, integration with Kubernetes admission controller, and Infrastructure as Code (IaC) security to help seamlessly integrate security into developer workflows.

Thales Cloud Protection & Licensing
MAY 18, 2022
RSA Conference 2022 Back to Physical - The Thrill of Meeting in Person! madhav. Thu, 05/19/2022 - 05:25. And just like that, RSA Conference 2022 is back in San Francisco ! However, the event will also be online for those who cannot be there in person. Initially scheduled for February this year, the conference will now take place from June 6-9. Thales is thrilled to be hosting booth #6253 in the Moscone Center.

Dark Reading
MAY 18, 2022
Last month attackers quickly reverse-engineered VMWare patches to launch RCE attacks. CISA warns it's going to happen again.
Let's personalize your content