Do You Have to Archive Slack Data for Regulatory Compliance?
Hanzo Learning Center
FEBRUARY 28, 2022
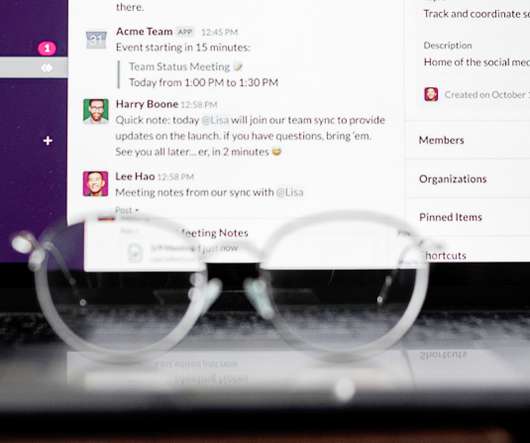
Is your organization required to archive its communications to comply with the laws, rules, and regulations that govern your industry? If so, the shift to remote work and the new business communications technologies like Slack for at least some of your internal and potentially external business communications may present a fertile new channel for consideration.






































Let's personalize your content