
News, news analysis, and commentary on the latest trends in cybersecurity technology.
Even with dedicated identity management tools at their disposal, many companies — smaller ones especially — are sticking with email and spreadsheets for handling permissions.
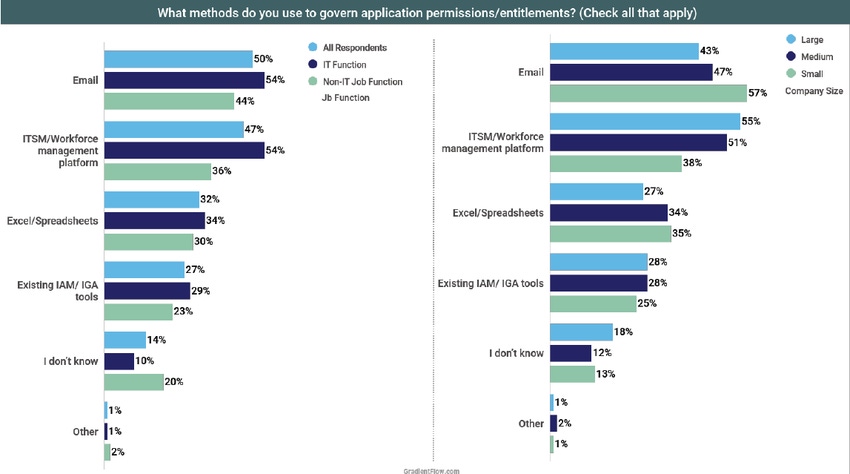
How do companies control application permissions and entitlements? According to a survey by Internet security and governance company Clear Skye, midsize and large companies turn to their IT service management (ITSM)/workforce management platform, while small companies are more inclined to use email.
The "2022 Identity Management Survey" polled a total of 514 respondents from a range of industries and organization sizes. Large companies are the most likely to place ITSM/workforce at the top of the list for controlling permissions, at 55%, while 51% of respondents from midsize companies did. The support dropped sharply for small companies, where only 38% reported using such software.
Small companies made up the difference by relying more heavily on email (57%) than either large (43%) or midsize (47%) organizations. Small and midsize companies were almost equally likely to use Excel or other spreadsheets to control permissions (35% and 34%, respectively), while large companies were less likely to use spreadsheets (27%).
Prepackaged identity and access management (IAM)/identity governance and administration (IGA) saw less than one-third penetration among large and midsize businesses (28% each), while small businesses were even less invested (25%).
And "invested" might be on the nose. Small businesses reported that cost was their top concern for permission management, while IT workers listed user experience, cost, and time to fulfillment as their top three challenges. After all, a company has to have an email system, and most also use spreadsheets already, so why introduce an expensive new system when you can rig an existing system to do mostly the same function?
Interestingly, respondents who had IT-specific job functions cited email and ITSM/workforce management as their top options for managing permissions and entitlements — 54% for each. Excel and other spreadsheets came in at a distant third place, with 34% of IT workers mentioning them. IAM/IGA tools beat out only "I don't know" (10%) and "other" (1%) in IT's estimation, with less than a third (29%) of IT workers citing that category. Non-IT workers at least have a good understanding of what their organizations use to control access, since their answers closely approached their IT colleagues.' Only "I don't know" was higher (10%), which makes sense.
Download the full report from Clear Skye.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024

