Okta, Microsoft Confirm Breaches Connected to Lapsus$ Hack
Data Breach Today
MARCH 23, 2022
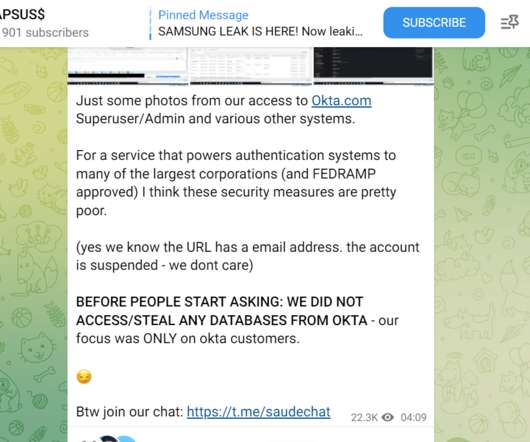
Okta Is Facing Increasing Pressure to Release More Details Identity management company Okta and Microsoft have confirmed breaches by the Lapsus$ group, which has been on a high-profile hacking spree. Okta is facing increasing pressure to more fully describe the impact of its incident, as Okta's identity systems are widely used across enterprises.








































Let's personalize your content