Hackers Stealing and Selling VoIP Access
Data Breach Today
NOVEMBER 9, 2020
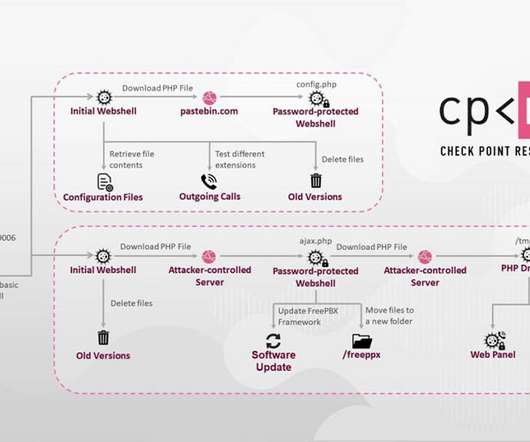
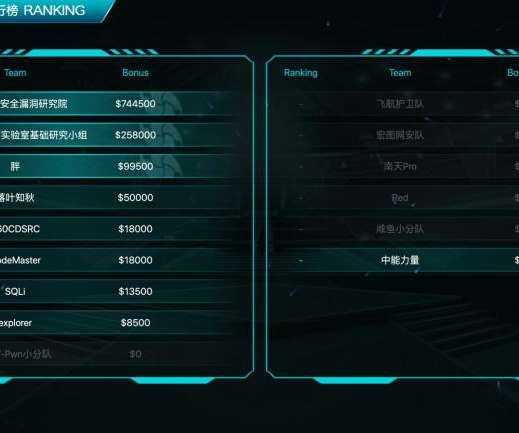
Attackers Exploit a Vulnerability in Asterisk VoIP PBX Servers Check Point Research has uncovered a large and likely profitable business model that involves hackers attacking and gaining control of certain VoIP services, which enables them to make phone calls through a company's compromised system.





































Let's personalize your content