Cyber Insurance: Important Lessons for New Markets
Data Breach Today
JANUARY 5, 2020
One of the major challenges for CISOs is on deciding the indemnity limit for cyber insurance, says Bhishma Maheshwari, executive vice president at Marsh India.

Data Breach Today
JANUARY 5, 2020
One of the major challenges for CISOs is on deciding the indemnity limit for cyber insurance, says Bhishma Maheshwari, executive vice president at Marsh India.

Security Affairs
JANUARY 5, 2020
Synoptek, A California-based IT service provider decided to pay the ransom to decrypt its files after being infected with the Sodinokibi ransomware. Synoptek, a California-based provider of IT management and cloud hosting services paid the ransom to decrypt its files following a Sodinokibi ransomware attack. The gang behind the Sodinokibi ransomware has been very active in the US in recent weeks, in December, CyrusOne, one of the major US data center provider, was hit by the same ransomware.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
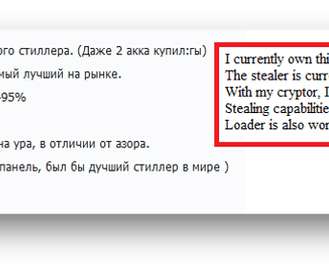
Security Affairs
JANUARY 5, 2020
DeathRansom was considered fake ransomware due to the fact that it did not implement an effective encryption process, but now things are changing. DeathRansom is a ransomware family that was initially classified as a joke because it did not implement an effective encryption scheme. Researchers at Fortinet published an analysis that shows the threat evolving, it is now capable of encrypting files using strong encryption.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

eDiscovery Daily
JANUARY 5, 2020
Hindsight is 2020. Get it? ; o ) With that in mind, 2019 was another notable year for eDiscovery case law with several significant rulings that stand to impact eDiscovery practices, the admissibility of evidence and the potential of sanctions for discovery violations. How can these key case law decisions affect discovery within your organization?
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

John Battelle's Searchblog
JANUARY 5, 2020
A new year brings another run at my annual predictions: For 17 years now, I’ve taken a few hours to imagine what might happen over the course of the coming twelve months. And my goodness did I swing for the fences last year ?—?and I pretty much whiffed. Batting .300 is great in the majors, but it kind of sucks compared to my historical average. My mistake was predicting events that I wished would happen.
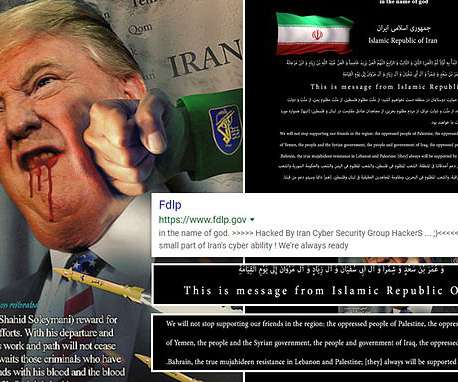
Security Affairs
JANUARY 5, 2020
A group of alleged Iranian hackers claims to have breached the website of a US government agency, Federal Depository Library Program , on Saturday after the killing of Qasem Soleimani. A group of Iranian hackers claims to have breached the website of a US government agency, the Federal Depository Library Program, vowing revenge for the killing of commander Qasem Soleimani.
Let's personalize your content