The FTC Wants Companies to Find Log4j Fast. It Won't Be Easy
WIRED Threat Level
JANUARY 10, 2022
The critical vulnerability is buried among endless open source code, and many cyber experts are stumped.

WIRED Threat Level
JANUARY 10, 2022
The critical vulnerability is buried among endless open source code, and many cyber experts are stumped.

Thales Cloud Protection & Licensing
JANUARY 10, 2022
How Can We Secure The Future of Digital Payments? divya. Tue, 01/11/2022 - 06:35. The financial services ecosystem has evolved tremendously over the past few years driven by a surge in the adoption of digital payments. This raises the question of where digital payment technologies will take us in the future, and how will this affect consumers? In the latest episode of Thales Security Sessions podcast , I was asked by Neira Jones to join Simon Keates, Head of Strategy and Payment Security at Thal
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
JANUARY 10, 2022
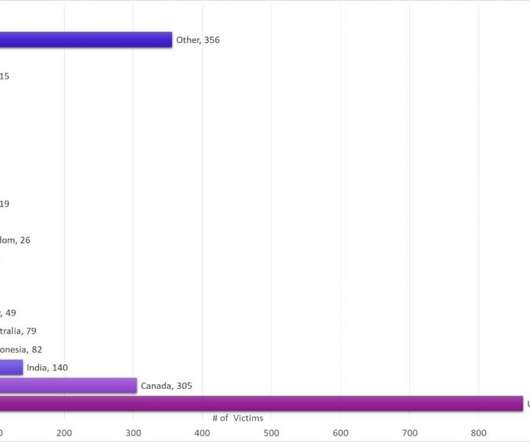
A malware campaign spreads ZLoader malware by exploiting a Windows vulnerability that was fixed in 2013 but in 2014 Microsoft revised the fix. Experts from Check Point Research uncovered a new ZLoader malware campaign in early November 2021. The malware campaign is still active and threat actors have already stolen data and credentials of more than 2000 victims across 111 countries as of 2 Jan 2022.

OpenText Information Management
JANUARY 10, 2022
As we head into 2022, it’s clear that the Financial Services industry overall has responded well to the impact of COVID-19 — but it hasn’t emerged unscathed. In fact, McKinsey’s Global Banking Review states that half of banks are not covering their cost of equity. The future remains uncertain apart from one thing: Financial Services … The post Key trends for the Financial Services industry in 2022 appeared first on OpenText Blogs.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

The Guardian Data Protection
JANUARY 10, 2022
EU police body accused of unlawfully holding information and aspiring to become an NSA-style mass surveillance agency The EU’s police agency, Europol, will be forced to delete much of a vast store of personal data that it has been found to have amassed unlawfully by the bloc’s data protection watchdog. The unprecedented finding from the European Data Protection Supervisor (EDPS) targets what privacy experts are calling a “big data ark” containing billions of points of information.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

IT Governance
JANUARY 10, 2022
For many, 2021 was a year to forget. COVID-19 again dominated the news, with initial optimism over vaccine rollouts and the potential end of the pandemic making way for new variants and the return of social restrictions. The cyber security landscape offered similarly familiar topics: there were huge data breaches at Facebook and LinkedIn, while the threat of ransomware reached catastrophic levels.

Dark Reading
JANUARY 10, 2022
In the wake of WannaCry and its ilk, the National Vulnerability Database arose to help security organizations track and prioritize vulnerabilities to patch. Part 1 of 3.

Threatpost
JANUARY 10, 2022
Dangerous security bugs stemming from widespread inconsistencies among 16 popular third-party URL-parsing libraries could affect a wide swath of web applications.

Dark Reading
JANUARY 10, 2022
Companies are more likely to rely on outside attorneys to handle cyber response in order to contain potential lawsuits. Meanwhile, cyber-insurance premiums are rising but covering less.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
JANUARY 10, 2022
Several EA Sports FIFA 22 players claim to have been hacked, they say to have lost access to their personal EA and email accounts. A growing number of EA Sports FIFA 22 players reported that their EA accounts were hacked, including famous streamers such as Jamie Bateson (AKA Bateson87), NickRTFM, Trymacs, TisiSchubecH and FUT FG. Attackers also stole coins and players from the FUT clubs of the gamers.

Schneier on Security
JANUARY 10, 2022
The City of Austin is warning about QR codes stuck to parking meters that take people to fraudulent payment sites.

Security Affairs
JANUARY 10, 2022
WordPress maintainers have released WordPress 5.8.3 that addresses four vulnerabilities and recommend admins to update their sites immediately. The WordPress 5.8.3 security release addresses four vulnerabilities affecting versions between 3.7 and 5.8, it is labeled as a short-cycle security release. The organization announced that the next major release will be version 5.9 , which is already in the Release Candidate stage.

Dark Reading
JANUARY 10, 2022
An FBI warning says the FIN7 cybercrime group has sent packages containing malicious USB drives to US companies in an effort to spread ransomware.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Threatpost
JANUARY 10, 2022
Cyberattacks increased 50 percent YoY in 2021 and peaked in December due to a frenzy of Log4j exploits, researchers found.
Security Affairs
JANUARY 10, 2022
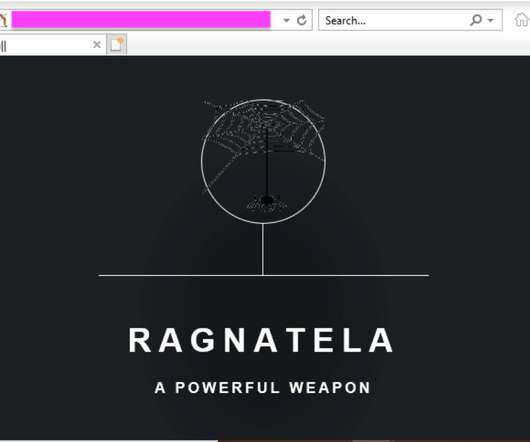
The India-linked threat actor Patchwork infected one of their own computers with its RAT revealing its operations to researchers. An India-linked threat actor, tracked as Patchwork (aka Dropping Elephant), employed a new variant of the BADNEWS backdoor, dubbed Ragnatela (“spider web” in Italian), in a recent campaign. However, the group made the headlines after infecting its infrastructure with a RAT allowing researchers to analyze its operations.
John Battelle's Searchblog
JANUARY 10, 2022
If you want to follow the debate about crypto’s impact on society, which I believe is one of the most important topics in tech today, you better sharpen your Twitter skills – most of the interesting thinking is happening across Twitter’s decidedly chaotic platform. I’ve been using the service for nearly 15 years, and I still find it difficult to bring to heel.
Security Affairs
JANUARY 10, 2022
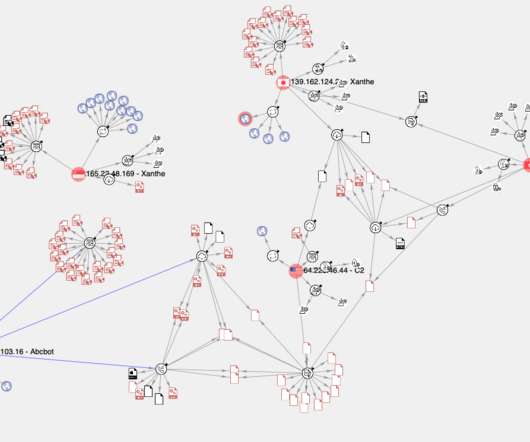
Experts linked the C2 infrastructure behind an the Abcbot botnet to a cryptocurrency-mining botnet attack that was uncovered in December 2020. Experts linked the infrastructure used by the Abcbot DDoS botnet to the operations of a cryptocurrency-mining botnet that was uncovered in December 2020. In November Researchers from Qihoo 360’s Netlab security team have spotted a new botnet, tracked as Abcbot, that targets Linux systems to launch distributed denial-of-service (DDoS) attacks.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Dark Reading
JANUARY 10, 2022
When security leaders look for mistakes, they often find them before customers do.

IG Guru
JANUARY 10, 2022
Check out her post on LinkedIn here. The post Susan B. Whitmire announces retirement after 45 years in RIM/IG appeared first on IG GURU.

Dark Reading
JANUARY 10, 2022
The vulnerability could allow an attacker to bypass the macOS Transparency, Consent, and Control measures to access a user's protected data.

OpenText Information Management
JANUARY 10, 2022
Organizations struggle to find quick and easy deployments of content management solutions that address specific departmental needs, and users struggle with content heavy processes for their many projects and daily tasks. These issues often lead to: Time-consuming system customizations set up by administrators Project delays across various departments Low adoption of technology Frustrated and unhappy users With purpose-built, … The post Accelerating user adoption through easily deployed of

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
JANUARY 10, 2022
The vulnerability could allow an attacker to bypass the macOS Transparency, Consent, and Control measures to access a user's protected data.

The Last Watchdog
JANUARY 10, 2022
Working with personal data in today’s cyber threat landscape is inherently risky. Related: The dangers of normalizing encryption for government use. It’s possible to de-risk work scenarios involving personal data by carrying out a classic risk assessment of an organization’s internal and external infrastructure. This can include: Security contours. Setting up security contours for certain types of personal data can be useful for: •Nullifying threats and risks applicable to general infrastructura
eSecurity Planet
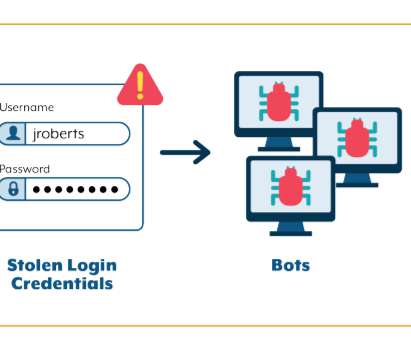
JANUARY 10, 2022
A report last week by the New York Attorney General’s Office put a spotlight on the ongoing threat of credential stuffing, a common technique used by cybercriminals that continues to spread and is helping to fuel the push for security practices that don’t involve usernames and passwords. AG Letitia James’ office ran a months-long investigation into credential attacks in the state, uncovering credentials for more than 1.1 million online accounts at 17 companies, including online retailers, restau
Let's personalize your content