APTs Using New Tools to Target ICS/SCADA
Data Breach Today
APRIL 14, 2022
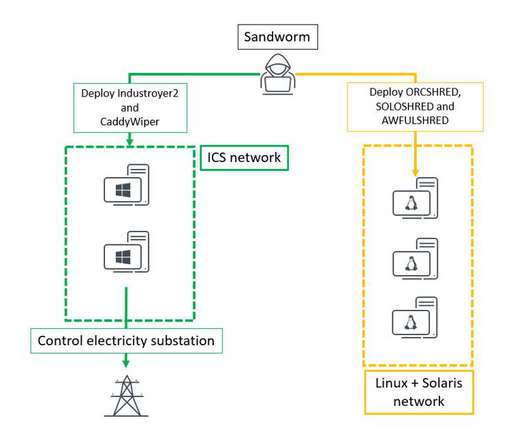
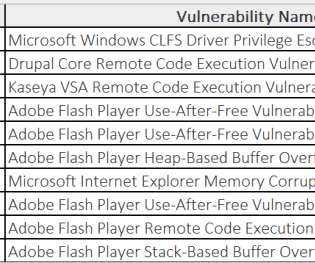
US Government Agencies, Mandiant, Dragos, Schneider Electric Issue Joint Advisory U.S. government agencies, including the Department of Energy, CISA, the NSA and the FBI issued a joint cybersecurity advisory about advanced persistent threat actors using new tools and malwares to target industrial control systems and supervisory control and data acquisition devices.







































Let's personalize your content