So, Your MFA is Phishable, What To Do Next
KnowBe4
AUGUST 31, 2022
We’ve written a lot about multi-factor authentication (MFA) not being the Holy Grail to prevent phishing attacks, including here:

KnowBe4
AUGUST 31, 2022
We’ve written a lot about multi-factor authentication (MFA) not being the Holy Grail to prevent phishing attacks, including here:

Data Breach Today
AUGUST 31, 2022
Criminal Underground Briefly Assisted But Quickly Grew Bored, Researchers Find The role and impact of criminal hackers and volunteer hacktivists in the Russia-Ukraine war has been vastly overestimated, a team of cybersecurity researchers report, based not just on charting distributed denial-of-service attacks and defacements but also on interviews with participants.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
AUGUST 31, 2022
Last year, I posted a series of articles about a purported “breach” at Ubiquiti. My sole source for that reporting was the person who has since been indicted by federal prosecutors for his alleged wrongdoing – which includes providing false information to the press. As a result of the new information that has been provided to me, I no longer have faith in the veracity of my source or the information he provided to me.

Data Breach Today
AUGUST 31, 2022
Federal Law Enforcement Agents Offer Tips on Improving Detection, Rapid Response Ransomware gets the headlines, and phishing sets off the most alerts, but business email compromise costs enterprises the most - more than $43 billion since 2016. U.S. Secret Service agents Stephen Dougherty and Michael Johns discuss the criticality of rapid detection and response.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
KnowBe4
AUGUST 31, 2022
Researchers at Check Point warn that attackers based in Turkey are distributing cryptomining malware via free software distribution websites, including Softpedia and uptodown. The malicious apps appear to be legitimate, but have malware packaged within them.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

KnowBe4
AUGUST 31, 2022
As threat actors look for ways to evade detection by security solutions, the use of cloud applications has seen a material jump in the last 12 months, according to new data.

Data Breach Today
AUGUST 31, 2022
CISOs have enough tools to identify security weaknesses, says Yoran Sirkis, but they need a way to make the information those tools gather more accessible and to streamline the remediation process. The CEO of Seemplicity discusses how its platform can help security leaders manage remediations.
eSecurity Planet
AUGUST 31, 2022
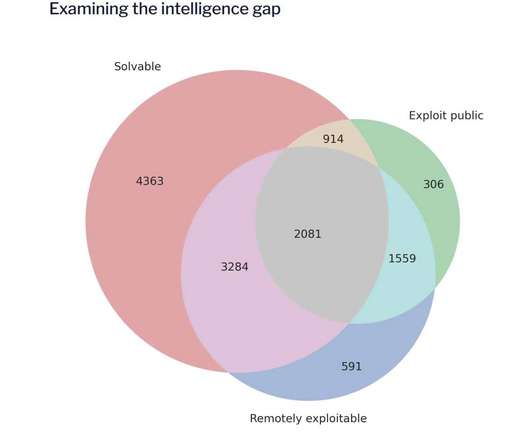
Vulnerability management systems based on the Common Vulnerability Scoring System (CVSS) v2 scoring system may be misguided, as a new report found that roughly half of the most critical vulnerabilities may be scored incorrectly. “Looking at the past 10 years, in the same midyear period, we see that on average, 51.5 percent of all known 10.0 scored vulnerabilities are unspecified,” Flashpoint noted in its mid-year 2022 Report. “This means organizations could be prioritizing hund

Data Breach Today
AUGUST 31, 2022
Proposed Class Action Comes in Wake of Big Hacking Incident A former employee of multistate senior living chain Avamere Health Services LLC has filed a proposed class action lawsuit accusing the company of negligence and other allegations in the wake of a hacking incident affecting her as well as 381,000 employees and patients.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

KnowBe4
AUGUST 31, 2022
After suffering a taste of their own medicine as part of a response effort from victim organization Entrust, LockBit appears to have bounced back even stronger than before.

Dark Reading
AUGUST 31, 2022
While cloud breaches are going to happen, that doesn't mean we can't do anything about them. By better understanding cloud attacks, organizations can better prepare for them. (First of two parts.

Security Affairs
AUGUST 31, 2022
Italian oil giant Eni was hit by a cyber attack, attackers compromised its computer networks, but the consequences appear to be minor. Italian oil giant company Eni disclosed a security breach, threat actors gained access to its network, but according to the company the intrusion had minor consequences because it was quickly detected. “The internal protection systems have detected unauthorized access to the corporate network in recent days,” a spokesperson for the company told Reuter

Dark Reading
AUGUST 31, 2022
The ongoing campaign is spreading worldwide, using the lure of a fully functional Google Translate application for desktops that has helped the threat stay undetected for months.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Security Affairs
AUGUST 31, 2022
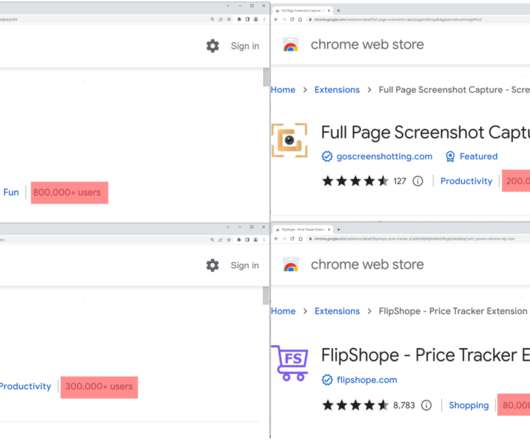
Researchers spotted 5 malicious Google Chrome extensions used to track users’ browsing activity and profit of retail affiliate programs. McAfee researchers discovered five malicious Google Chrome extensions with a total install base of over 1,400,000. The malicious Google Chrome extensions were masquerading as Netflix viewers, website coupons, and apps for taking screenshots of a website.

Threatpost
AUGUST 31, 2022
2.5 million people were affected, in a breach that could spell more trouble down the line.

Dark Reading
AUGUST 31, 2022
(ISC)² pledges to expand and diversify the cybersecurity workforce by providing free "(ISC)² Certified in Cybersecurity" education and exams to 1 million people worldwide.

Security Affairs
AUGUST 31, 2022
A malware campaign tracked as GO#WEBBFUSCATOR used an image taken from NASA’s James Webb Space Telescope (JWST) as a lure. Securonix Threat researchers uncovered a persistent Golang-based malware campaign tracked as GO#WEBBFUSCATOR that leveraged the deep field image taken from the James Webb telescope. The phishing emails contain a Microsoft Office attachment that includes an external reference in its metadata which downloads a malicious template file.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

KnowBe4
AUGUST 31, 2022
As cybercriminals continue to evolve their techniques, they continue to rely on phishing as the most successful tried and true method of initial attack, according to new data from Acronis.
Security Affairs
AUGUST 31, 2022
The Russian subscription-based streaming service Start discloses a data breach affecting 7.5 million users. The Russian media streaming platform START disclosed a data breach that impacted 7.5 millions of its users. According to the company, the attackers stole a 2021 database from its infrastructure and also shared a samples online to demonstrate the authenticity of the claims.

Dark Reading
AUGUST 31, 2022
But one issue that lets websites overwrite content on a user's system clipboard appears unfixed in the new Version 105 of Chrome.

Schneier on Security
AUGUST 31, 2022
This is a fun story, detailing the hack a group of high school students perpetrated against an Illinois school district, hacking 500 screens across a bunch of schools. During the process, the group broke into the school’s IT systems; repurposed software used to monitor students’ computers; discovered a new vulnerability (and reported it ); wrote their own scripts; secretly tested their system at night; and managed to avoid detection in the school’s network.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
AUGUST 31, 2022
OpenText makes a $6 billion bet that bigger is better in security and that cybersecurity platform plays are the future.

Thales Cloud Protection & Licensing
AUGUST 31, 2022
Financial services continue to lead in cybersecurity preparedness, but chinks appear in the armor. divya. Thu, 09/01/2022 - 05:15. Organizations in the finance sector manage trillions of dollars and maintain very valuable and vital electronic data, including bank account, credit card, and transaction information as well as sensitive data related to estates, wills, titles, and other matters.

Dark Reading
AUGUST 31, 2022
New Golang cyberattacks use deep space images and a new obfuscator to target systems — undetected.

Hunton Privacy
AUGUST 31, 2022
On August 29, 2022, the Federal Trade Commission released the agenda for its virtual public forum on the Commercial Surveillance and Data Security Advanced Notice of Public Rulemaking. The forum, to be held on September 8, 2022, seeks “public comment on the harms stemming from commercial surveillance and lax data security practices and whether new rules are needed to protect people’s privacy and information.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Dark Reading
AUGUST 31, 2022
Next-gen platform delivers adaptive and robust, continuous authentication with identity orchestration and a frictionless user experience.
WIRED Threat Level
AUGUST 31, 2022
Plus: Chrome patches another zero-day flaw, Microsoft closes up 100 vulnerabilities, Android gets a significant patch, and more.

Dark Reading
AUGUST 31, 2022
No-code startups such as Mine PrivacyOps say they offer best of both worlds — quick development and compliance with privacy laws.
Let's personalize your content