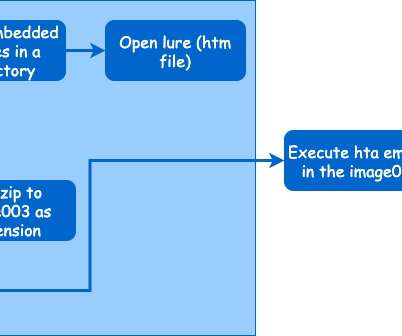
XCSSET Malware Can Adapt to Target More Macs
Data Breach Today
APRIL 20, 2021
Trend Micro Describes the Evolving Threat The XCSSET malware campaign can now adapt to target a wider variety of Macs, including those with the M1 chip, according to Trend Micro researchers.







































Let's personalize your content