Scammers Impersonate OpenSea Customer Support
Data Breach Today
AUGUST 31, 2021
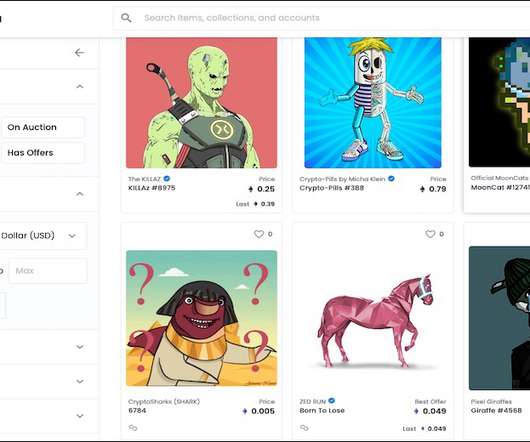
Attackers Socially Engineer Digital Asset Holders on Discord Users of OpenSea, a marketplace for blockchain-based digital assets such as crypto collectibles and non-fungible tokens, are being targeted by scammers pretending to be the company's support staff on Discord. The attackers exploited a method OpenSea uses to service support tickets on Discord.







































Let's personalize your content