Twitter Hack: Suspects Left Easy Trail for Investigators
Data Breach Today
AUGUST 4, 2020
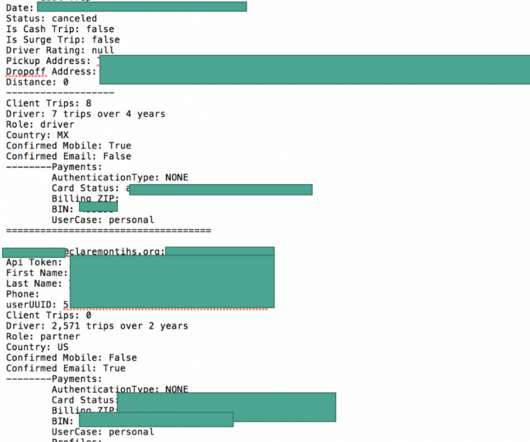
Bitcoin Accounts Linked to Driver's Licenses, Leading to Arrests Suspects in the epic attack against Twitter were uncovered in part by the use of their real photo identification for cryptocurrency accounts they used to broker the sale of stolen usernames. The mistakes proved crucial to their identification, according to court documents.






































Let's personalize your content