Hackers exploit SQL injection zero-day issue in Sophos firewall
Security Affairs
APRIL 26, 2020
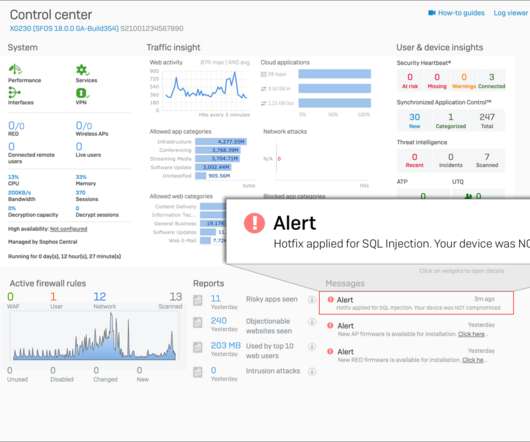
Cybersecurity firm Sophos releases an emergency patch to address an SQL injection flaw in its XG Firewall product that has been exploited in the wild. Cybersecurity firm Sophos has released an emergency patch to address an SQL injection zero-day vulnerability affecting its XG Firewall product that has been exploited in the wild. Sophos was informed of the attacks exploiting the zero-day issue by one of its customers on April 22.












Let's personalize your content