Siemens Metaverse exposes sensitive corporate data
Security Affairs
APRIL 15, 2023
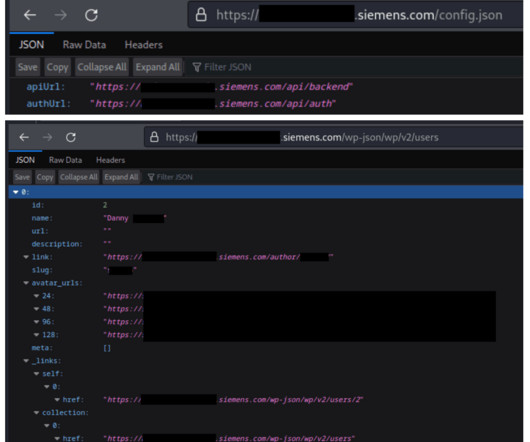
Siemens Metaverse, a virtual space built to mirror real machines, factories, and other highly complex systems, has exposed sensitive data, including the company’s office plans and internet of things (IoT) devices. While metaverse is no longer a buzzword, amid the sudden popularity of ChatGPT and similar AI tools, those virtual worlds are still here, presenting exciting opportunities for companies, users, and, unfortunately, threat actors.













Let's personalize your content