Putting Cyberthreat Intelligence Data Into Action
Data Breach Today
JUNE 30, 2022
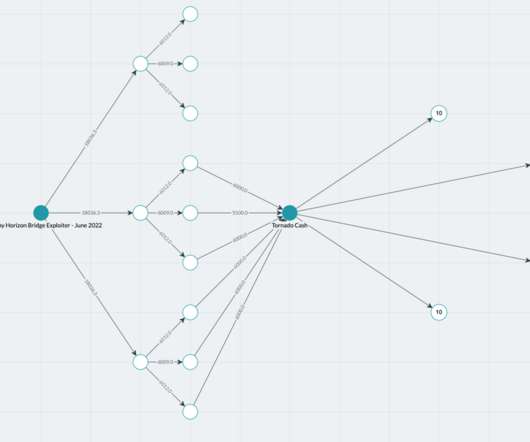
How can CISOs put the cyberthreat intelligence data they receive into practice? Kunal Sehgal, former director of global cyber resilience at Standard Chartered Bank, discusses how different industries use cyberthreat intelligence and explains misconceptions about sharing information.





































Let's personalize your content