What Went Wrong at Equifax? We Have Good Answers
Data Breach Today
APRIL 3, 2020
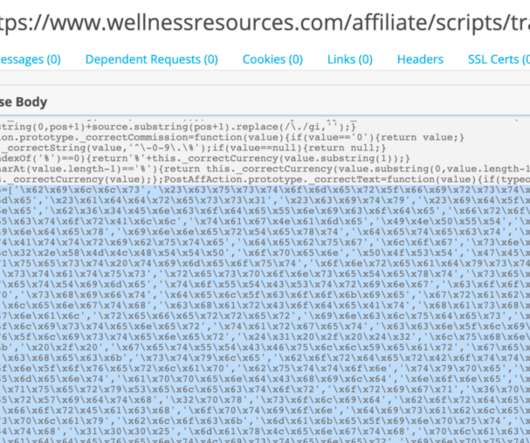
What missteps led to hackers stealing details on 145 million Americans from Equifax in 2017? The answer to that question can be found in numerous reports and a Justice Department indictment. Security researcher Adrian Sanabria says they're essential reading for anyone responsible for cybersecurity defenses.





































Let's personalize your content