Why Are We So Stupid About Passwords? SSH and RDP Edition
Data Breach Today
OCTOBER 21, 2022
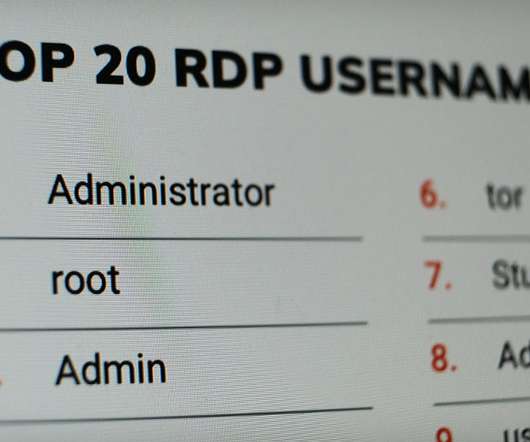
Poor Credential Hygiene Leaves Remote Services at Risk of Brute Force Attacks If remote access to corporate networks is only as secure as the weakest link, only some dreadfully weak passwords now stand between hackers and many organizations' most sensitive data, according to new research from Rapid7 into the two most widely used remote access protocols - SSH and RDP.








































Let's personalize your content