Understanding the Human Communications Attack Surface
Dark Reading
NOVEMBER 1, 2021
Companies should recognize that collaboration platforms aren't isolated, secure channels where traditional threats don't exist.

Dark Reading
NOVEMBER 1, 2021
Companies should recognize that collaboration platforms aren't isolated, secure channels where traditional threats don't exist.

Data Breach Today
NOVEMBER 1, 2021
Operators Left Exposed After Overreaching, Says McAfee Enterprise’s John Fokker How is the ransomware ecosystem set to evolve? Since some operations overreached - notably with DarkSide's hit on Colonial Pipeline - "what we're seeing … is that there is going to be a power balance shift," says McAfee's John Fokker, with more affiliates, not gang leaders, calling the shots.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
NOVEMBER 1, 2021
The US FBI has published a flash alert warning private organizations of the evolution of the HelloKitty ransomware (aka FiveHands). The U.S. Federal Bureau of Investigation (FBI) has sent out a flash alert warning private industry of a new feature of the HelloKitty ransomware gang (aka FiveHands). According to the alert, the ransomware gang is launching distributed denial-of-service (DDoS) attacks as part of its extortion activities. “Hello Kitty/FiveHands actors aggressively apply pressur

Data Breach Today
NOVEMBER 1, 2021
This Flaw Could Lead to an Attack Like SolarWinds Two researchers from the University of Cambridge have discovered a vulnerability that affects most computer code compilers and many software development environments, according to a new research paper. The bug could cause a SolarWinds-like open-source supply chain attack scenario, they say.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Schneier on Security
NOVEMBER 1, 2021
Really interesting research demonstrating how to hide vulnerabilities in source code by manipulating how Unicode text is displayed. It’s really clever, and not the sort of attack one would normally think about. From Ross Anderson’s blog : We have discovered ways of manipulating the encoding of source code files so that human viewers and compilers see different logic.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
NOVEMBER 1, 2021
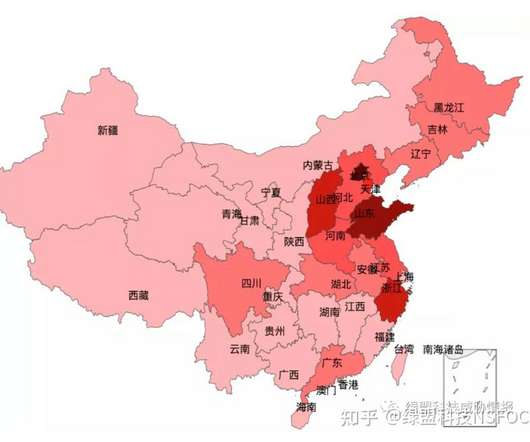
Cybersecurity researchers uncovered a huge botnet, tracked as Pink, that already infected over 1.6 million devices most of them located in China. Qihoo 360’s Netlab Cybersecurity researchers discovered a huge botnet, tracked as Pink, that already infected over 1.6 million devices. The botnet was created to launch DDoS attacks and to insert advertisements in the legitimate HTTP traffic of the victims, most of which are in China (96%).

Data Breach Today
NOVEMBER 1, 2021
HHS OCR: If Old Gear Cannot Be Replaced, Take Other Steps to Protect PHI Federal regulators are reminding healthcare organizations about the critical importance of addressing security risks involving legacy systems and devices - including specialty software and gear - that are often difficult for entities to replace. What steps should entities take?

DLA Piper Privacy Matters
NOVEMBER 1, 2021
US: Cyber Advisory: Feds Warn that Water Facilities Are Targets for Cyber Attacks. By Justine Phillips and Garrett Stallins. #DLAPiperCommodities. #DLAPiperCyber. On October 14, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigations, the Environmental Protection Agency, and the National Security Agency issued a joint advisory warning of active cyber threats to water and wastewater infrastructure in the United States.

Data Breach Today
NOVEMBER 1, 2021
Agency's Jen Easterly, Rep. John Katko Discuss Protection of U.S. Networks CISA Director Jen Easterly and congressional leader John Katko, R-N.Y., agree that officials must take precautionary steps to identify "systemically important critical infrastructure" to reduce risks of pervasive supply chain cyberattacks.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
Security Affairs
NOVEMBER 1, 2021
Operators behind the Squid Game cryptocurrency have exit scam making off with an estimated $2.1 million. Operators behind the Squid Game cryptocurrency have exit scam making off with an estimated $2.1 million just after a week from its launch. Gizmodo, which first reported the news , initially warned of a potential scam because investors were not allowed to sell the purchased crypto.

IT Governance
NOVEMBER 1, 2021
In October, we discovered 94 publicly disclosed cyber security incidents, accounting for 51,248,331 breached records. The majority of those records came from a cyber attack in which a hacker accessed Argentina’s government ID database, with every citizen of the country thought to be affected. However, there are plenty of other incidents to dig into, including a raft of ransomware attacks against the education sector.

Security Affairs
NOVEMBER 1, 2021
Researchers demonstrated how crooks could hack Diebold Nixdorf’s Wincor Cineo ATMs to bypass black-box attack protections and withdraw cash. Positive Technologies researchers Vladimir Kononovich and Alexey Stennikov have discovered security flaws Wincor Cineo ATMs that could be exploited to bypass Black-Box attack protections and withdraw cash. “According to Vladimir Kononovich, some manufacturers rely on security through obscurity, with proprietary protocols that are poorly studied

Dark Reading
NOVEMBER 1, 2021
A researcher will release an open source tool at Black Hat Europe next week that roots out server weaknesses to a sneaky type of attack.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Threatpost
NOVEMBER 1, 2021
The old RLO trick of exploiting how Unicode handles script ordering and a related homoglyph attack can imperceptibly switch the real name of malware.

Hunton Privacy
NOVEMBER 1, 2021
On October 29, 2021, the Cyberspace Administration of China (“CAC”) released for public comment “Draft Measures on Security Assessment of Cross-border Data Transfer” (“Draft Measures”). The CAC, in its third legislative attempt to build a cross-border data transfer mechanism in China, issued the Draft Measures three days before the November 1, 2021 effective date of the Personal Information Protection Law (“PIPL”).

DLA Piper Privacy Matters
NOVEMBER 1, 2021
China’s PIPL came into force today, and to accompany this, the Cyberspace Administration of China (“ CAC ”, the key data regulator) has published for consultation draft guidelines to assist organisations grappling with overseas data transfers with some practical guidance on some of the compliance steps that must be taken. Under the PIPL, certain organisations – or the overseas transfer of certain data categories – require the data controller to undertake a security impact assessment (“ SIA ”) in
eSecurity Planet
NOVEMBER 1, 2021
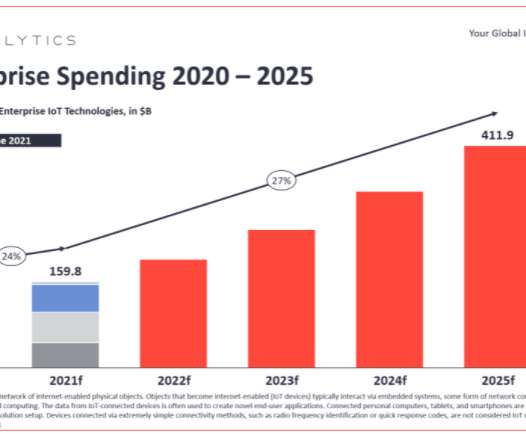
The European Union is poised to place more demands on manufacturers to design greater security into their wireless and Internet of Things (IoT) devices. In an amendment to the EU’s 2014 Radio Equipment Directive (RED), the European Commission noted that as wireless devices, from mobile phones to fitness trackers to smart watches, become increasingly embedded into everyday consumer and business life, they also become a greater security risk.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Security Affairs
NOVEMBER 1, 2021
Meet Balikbayan Foxes: a threat group impersonating the Philippine gov’t. Experts uncovered a new threat actor, tracked as Balikbayan Foxes, that is impersonating the Philippine government to spread malware. . Researchers from Proofpoint have uncovered a new threat actor, dubbed Balikbayan Foxes (TA2722) that is impersonating the Philippine health, labor, and customs organizations as well as other entities based in the Philippines to spread Trojan malware such as Remcos and NanoCore.

Threatpost
NOVEMBER 1, 2021
An alleged sports content pirate is accused of not only hijacking leagues' streams but also threatening to tell reporters how he accessed their systems.

WIRED Threat Level
NOVEMBER 1, 2021
The popular marketplace’s closing leaves a big hole in the billion-dollar industry of illegal drugs, credit card and bank fraud, forged documents, and more.

IG Guru
NOVEMBER 1, 2021
Check out the article here. The post Scare or Scarcity? Crowley still able to deliver Mekel Technology scanners on time despite worldwide microchip squeeze. appeared first on IG GURU.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
NOVEMBER 1, 2021
Feeling creative? Come up with a clever caption, and our panel of experts will reward the winner with a $25 Amazon gift card.

Threatpost
NOVEMBER 1, 2021
It's a legitimate access token, stolen from a third-party contractor, that lets the attackers send phishing emails from kaspersky.com email addresses.

Dark Reading
NOVEMBER 1, 2021
CISA will host an election situational awareness room to coordinate with federal partners, state and local election officials, private sector election partners, and political organizations to share real-time information and provide support as needed.

OpenText Information Management
NOVEMBER 1, 2021
Background – Global financial institution seeks to modernize web content management strategy A global bank and longtime OpenText™ TeamSite™ customer with 86,000+ employees serving over 17 million clients in 27 countries, needed a robust, scalable content management system to support creating, personalizing, and delivering content across internal business units, external communications and applications and customer-facing omnichannel solutions.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Dark Reading
NOVEMBER 1, 2021
Fresh off a $250 million Series E round, Devo Technology plans to expand the core security analytics platform with new features to help enterprise defenders work with security data faster and more effectively.

Adapture
NOVEMBER 1, 2021
The New State of HR & How You Should Hire for It. After the chaos of 2020, with its pandemic closures unexpected deep dive into remote work, the state of HR has seismically shifted. During lockdowns, employees reaped the benefits of working from home with no commute, having a greater sense of work-life balance, being able to spend more time with family, and working on their own schedules.

Dark Reading
NOVEMBER 1, 2021
Researchers discover a new technique attackers could use to encode vulnerabilities into software while evading detection.
Let's personalize your content