Facebook Data Exposure: Lessons to Learn
Data Breach Today
APRIL 5, 2021
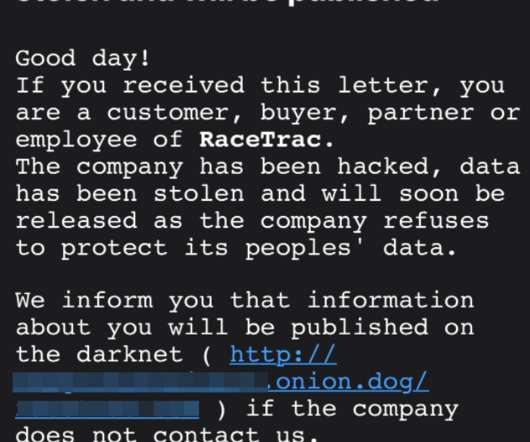
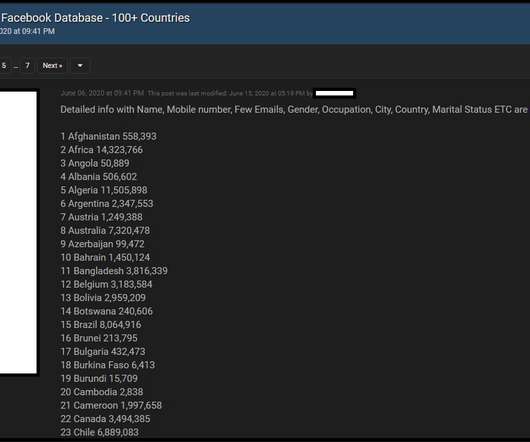
Experts Advise Organizations to Check Password Reset Policies, Take Other Steps The revelation that 533 million previously stolen Facebook account records have been made public on a darknet forum should inspire organizations to take aggressive action to further protect customer data security, some security experts say.







































Let's personalize your content