WiFi: A New Way to Spread Emotet Malware
Data Breach Today
FEBRUARY 11, 2020
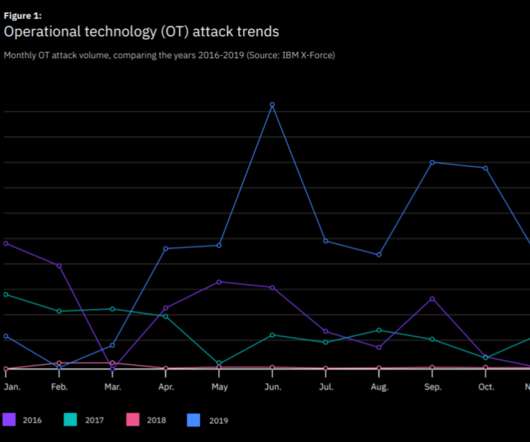
Researchers Say Trojan's Developers Devising Ways to Spread Trojan to More Devices Security researchers have found that the developers of the Emotet Trojan have created a new way to spread it to more victims - attackers are using unsecured WiFi networks as a way to deliver the malware to more devices.


































Let's personalize your content