How Ransomware Attackers Hit Virtual Machine Hypervisors
Data Breach Today
OCTOBER 5, 2021
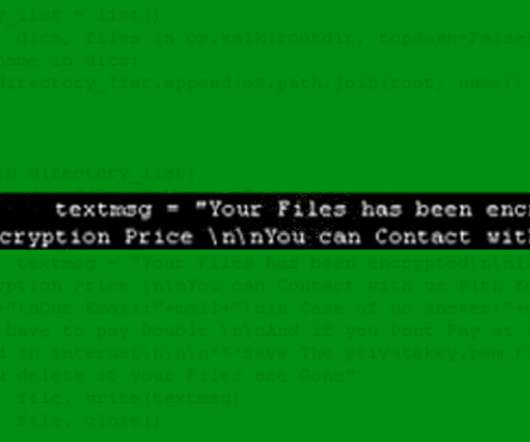
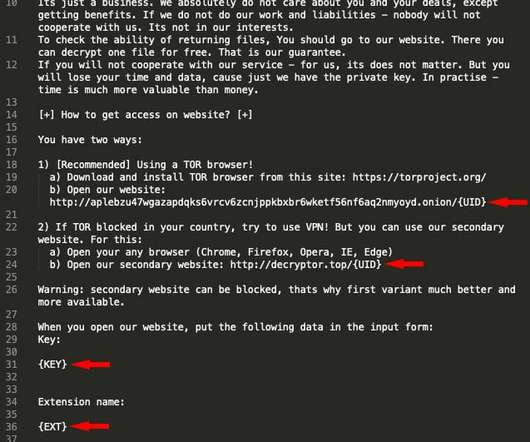
BlackMatter, HelloKitty and REvil Among Groups Targeting VMware's ESXi Hypervisor Hypervisors under fire: BlackMatter, HelloKitty and REvil are among the ransomware groups targeting instances of VMware's ESXi. In one case investigated by security firm Sophos, after first accessing a TeamViewer account, attackers left an organization's ESXi environment crypto-locked just three hours later.







































Let's personalize your content