Researchers: 25 Countries Use 'Circles' Spyware
Data Breach Today
DECEMBER 3, 2020
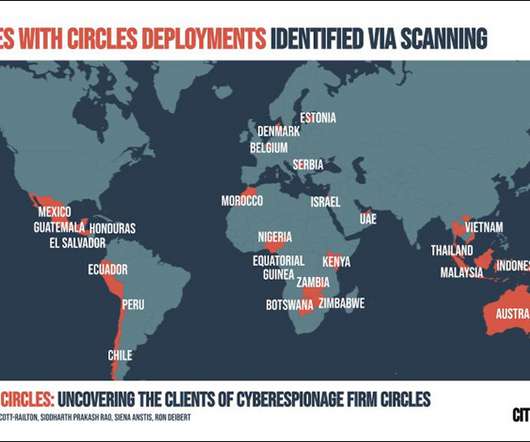
Application Tracks Individuals via Mobile Phones Twenty-five countries are likely using spyware sold by a company called Circles that can snoop on mobile phone calls and text messages, according to Citizen Lab, a research organization based at the University of Toronto.






































Let's personalize your content