Biden Faces Russian Ransomware Curtailment Challenge
Data Breach Today
JULY 8, 2021
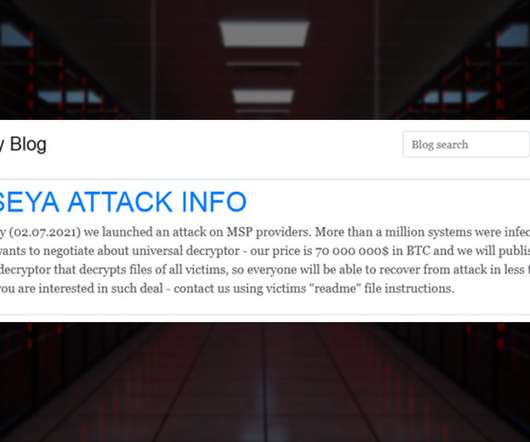
White House Tells Moscow: Take Action, or We 'Reserve the Right' to Do So The Biden administration has a message for Russia: Rein in the criminal hackers operating from inside your borders who hit Western targets, or we'll do it for you. But experts say disrupting ransomware will take more than diplomacy or even using offensive cyber operations to target criminal infrastructure.
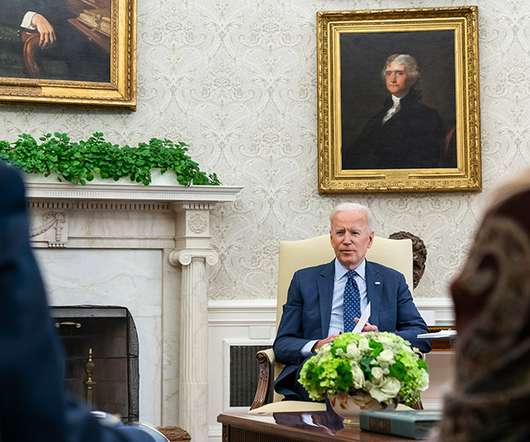





































Let's personalize your content