Malware Targets Kubernetes Clusters
Data Breach Today
FEBRUARY 4, 2021
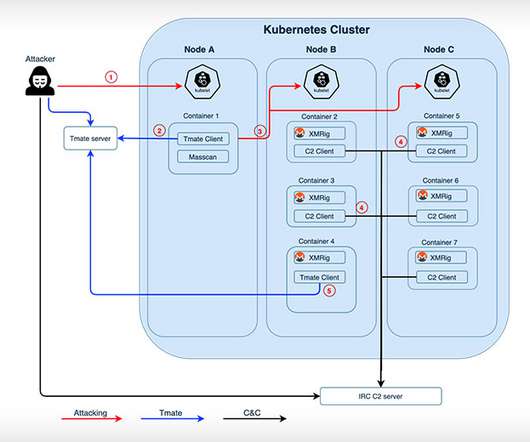
Researchers: 'Hildegard' Linked to TeamTNT Hacking Group A previously undocumented malware variant called "Hildegard" is targeting Kubernetes clusters, according to Palo Alto Networks' Unit 42. The malicious code is likely the work of the TeamTNT hacking group, which mines for monero cryptocurrency.







































Let's personalize your content