Sizing Up Nation-State Cyberthreats to the US Election
Data Breach Today
OCTOBER 27, 2020
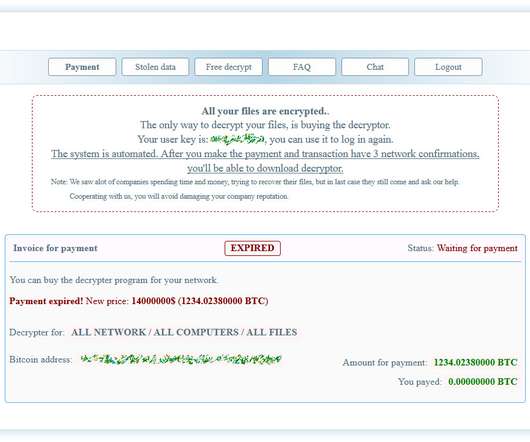
Digital Shadows: Disinformation, Ransomware, Phishing Attacks Prevail Online disinformation campaigns by nation-state actors are the biggest cyberthreat to the U.S. election as hackers attempt to influence final vote tallies as a way to undermine confidence, according to a Digital Shadows report. Russian hackers are most active, followed by Iran and China.



































Let's personalize your content