Are We Secure Yet? How to Build a 'Post-Breach' Culture
Dark Reading
JANUARY 20, 2020
There are many ways to improve your organization's cybersecurity practices, but the most important principle is to start from the top.

Dark Reading
JANUARY 20, 2020
There are many ways to improve your organization's cybersecurity practices, but the most important principle is to start from the top.

The Last Watchdog
JANUARY 20, 2020
Cyberattacks are becoming more prevalent, and their effects are becoming more disastrous. To help mitigate the risk of financial losses, more companies are turning to cyber insurance. Related: Bots attack business logic Cyber insurance, like other forms of business insurance, is a way for companies to transfer some of numerous potential liability hits associated specifically with IT infrastructure and IT activities.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
JANUARY 20, 2020
Report: Methods Make Payments Difficult to Track Cybercriminals are using increasingly sophisticated methods to turn illicitly gained cryptocurrency into cash, which raises new concerns about enforcing anti-money laundering laws, according a report by Chainalysis.

Krebs on Security
JANUARY 20, 2020
A Georgia man who co-founded a service designed to protect companies from crippling distributed denial-of-service (DDoS) attacks has pleaded to paying a DDoS-for-hire service to launch attacks against others. Tucker Preston , 22, of Macon, Ga., pleaded guilty last week in a New Jersey court to one count of damaging protected computers by transmission of a program, code or command.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Data Breach Today
JANUARY 20, 2020
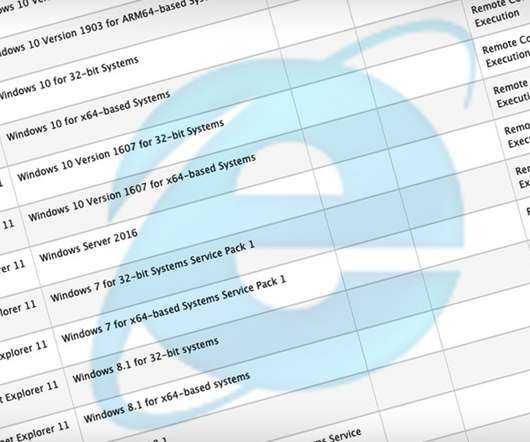
Patch Promised for Flaw Allegedly Exploited by 'DarkHotel' APT Gang Microsoft says it's prepping a patch to fix a memory corruption flaw in multiple versions of Internet Explorer that is being actively exploited by in-the-wild attackers, and issued mitigation guidance in the meantime. China's Qihoo 360 says the zero-day flaw has been exploited by the DarkHotel APT gang.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Breach Today
JANUARY 20, 2020
Researchers Discovered Software Flaw in December Citrix has released the first of several patches that address a vulnerability in its Application Delivery Controller and Gateway products that was discovered by researchers in December. If left unpatched, the vulnerability is remotely exploitable and could allow access to applications and internal networks.

Data Protection Report
JANUARY 20, 2020
2019 saw continued growth and change in data protection and cyber-security across the Asia-Pacific. Following the implementation of the GDPR in May, 2018, many jurisdictions moved to review and strengthen existing data privacy and cyber-security laws. In addition, 2019 saw regulators publishing findings in respect of some of the largest data incidents of 2018.

Data Breach Today
JANUARY 20, 2020
Deception technology is evolving as a powerful asset in the cybersecurity arsenal, providing significant advantages in being able to monitor an attacker's behavior, says Joseph Krull, senior analyst at Aite Group.

Security Affairs
JANUARY 20, 2020
Mitsubishi Electric disclosed a security breach that might have exposed personal and confidential corporate information. Mitsubishi Electric disclosed a security breach that might have exposed personal and confidential corporate data. According to the company, attackers did not obtain sensitive information about defense contracts. The breach was detected almost eight months ago, on June 28, 2019, with the delay being attributed to the increased complexity of the investigation caused by the attac

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
JANUARY 20, 2020
Could Attack on Florida Clinic Be Start of Disturbing Trend? Could cyberattacks on healthcare entities be taking an ugly twist? In a recent attack on a Florida-based plastic surgery practice, hackers exfiltrated patients' medical records and then demanded a ransom be paid by the clinic and some of its patients to avoid further exposure of the data.
Security Affairs
JANUARY 20, 2020
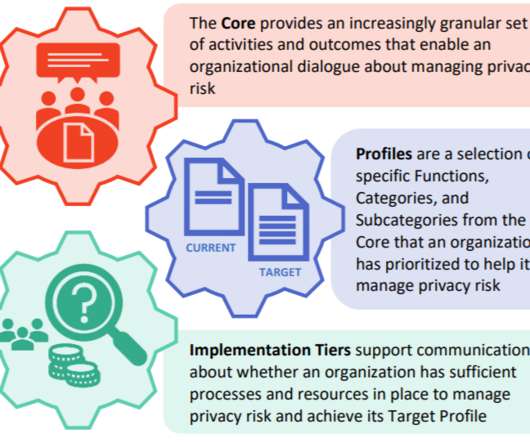
The NIST released version 1.0 of Privacy Framework, it is a tool designed to help organizations to manage privacy risks. The National Institute of Standards and Technology (NIST) has published the release version 1.0 of its privacy framework. The Framework is a voluntary tool that can be used by organizations to manage risks in compliance with privacy legislation, including the European GDPR.

Data Breach Today
JANUARY 20, 2020
DHS Would Fund Coordinators for Every State A bipartisan group of U.S. senators has introduced legislation that would require the Department of Homeland Security to appoint cybersecurity leaders in each state to help combat growing cyberthreats against units of local government.

Data Matters
JANUARY 20, 2020
A recent opinion from the European Data Protection Supervisor (EDPS) on data protection and scientific research builds on an opinion from January 2019 from the European Data Protection Board on the GDPR and clinical trials. The Opinion from the EDPS should be taken into account by life sciences companies in their ongoing assessment of how to apply the GDPR to scientific research both in clinical trials and more broadly.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Breach Today
JANUARY 20, 2020
Could satellites play a role in distributing next-generation encryption keys? Robert Bedington, CTO and co-founder at Singapore-based SpeQtral, describes quantum communications via satellites in this in-depth interview.

OpenText Information Management
JANUARY 20, 2020
Did you know that this year, 83% of enterprise workloads will run in the cloud? If you’re wondering how to begin your cloud journey, what you need to do to advance it or where you need to go to get your hands on everything cloud-journey related, the OpenText™ Cloud Summit is a must-attend event for … The post Start your cloud journey at Cloud Summit appeared first on OpenText Blogs.

HL Chronicle of Data Protection
JANUARY 20, 2020
On January 15, the Court of Justice of the European Union’s (CJEU) Advocate General (AG) Manuel Campos Sánchez-Bordona delivered his Opinion on four references for preliminary rulings on the topic of retention of and access to communications data. Of the four references, two originated from France, one from Belgium, and one from the Investigatory Powers Tribunal (IPT) in the United Kingdom.

Schneier on Security
JANUARY 20, 2020
The New York Times has a long story about Clearview AI, a small company that scrapes identified photos of people from pretty much everywhere, and then uses unstated magical AI technology to identify people in other photos. His tiny company, Clearview AI, devised a groundbreaking facial recognition app. You take a picture of a person, upload it and get to see public photos of that person, along with links to where those photos appeared.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

John Battelle's Searchblog
JANUARY 20, 2020
Google’s (and now Alphabet’s) CEO opines in the FT ( sub required ) on why AI needs to be regulated, joining the chorus of tech leaders who have taken the apparent high road when it comes to regulation, even as governments around the world have shown next to no ability to actually regulate anything (well, I guess the Chinese have certainly regulated tech…in a not so great way ).

Security Affairs
JANUARY 20, 2020
The Chairman of the NATO Military Committee announced that the alliance has sent a counter-hybrid team to Montenegro to face Russian hybrid attacks. Last week in Brussels, the Chairman of the NATO Military Committee (MC), Marshal Sir Stuart Peach, announced the effort of the Alliance in facing Russian hybrid attacks. The term “ Hybrid warfare ” refers to a military strategy which employs political warfare and blends conventional warfare, irregular warfare and cyberwarfare with other

Info Source
JANUARY 20, 2020
Receives the most Winter 2020 Pick awards in the industry. MONTVALE, N.J., Jan. 15, 2020 — Sharp Imaging and Information Company of America (SIICA), a division of Sharp Electronics Corporation (SEC), today announces that Sharp has earned a total of 14 Pick awards for Winter 2020, the most Keypoint Intelligence – Buyers Lab 2020 Pick awards in the Copier MFP category compared to all other competitors.
Security Affairs
JANUARY 20, 2020
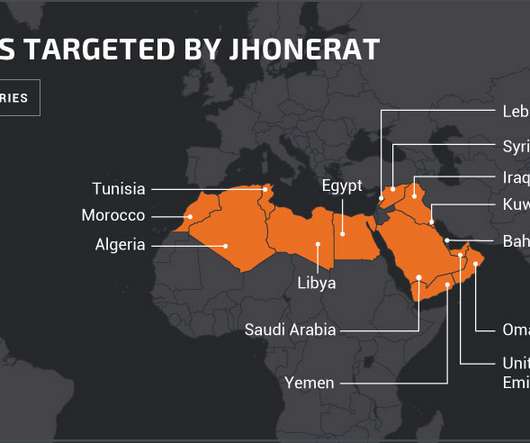
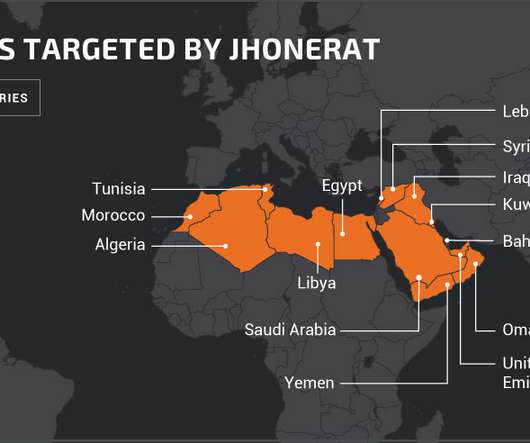
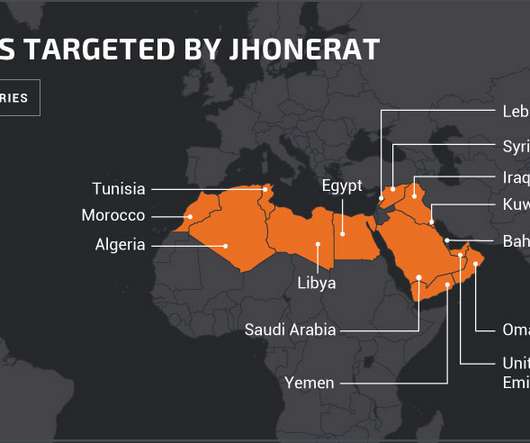
Researchers from Cisco Talos discovered a new Trojan named JhoneRAT that was used in targeted attacks against entities in the Middle East. A new Trojan named JhoneRAT appeared in the threat landscape, it is selectively attacking targets in the Middle East by checking keyboard layouts. The malware targets a very specific set of Arabic-speaking countries, including Saudi Arabia, Iraq, Egypt, Libya, Algeria, Morocco, Tunisia, Oman, Yemen, Syria, UAE, Kuwait, Bahrain, and Lebanon. “Today, Cisc

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

OpenText Information Management
JANUARY 20, 2020
IDEA (Industry Data Exchange Association) was established by the National Electrical Manufacturers Association and the National Association of Electrical Distributors in 1998 to provide manufacturers and distributors with the latest tools and technology to manage their operations effectively. To meet their objectives, IDEA needed new technology to support IDEA Exchange, the organization’s electronic data interchange … The post IDEA powers the electrical industry with OpenText Alloy appeare
Security Affairs
JANUARY 20, 2020
The WP Database Reset WordPress plugin is affected by an “easily exploitable” vulnerability that can allow attackers to take over vulnerable sites. . Security experts from Wordfence discovered two security vulnerabilities in the WP Database Reset WordPress plugin that can van be used to take over the vulnerable websites. The WordPress Database Reset plugin allows users to reset the database (all tables or the ones you choose) back to its default settings without having to go through

Dark Reading
JANUARY 20, 2020
There are many ways to improve your organization's cybersecurity practices, but the most important principle is to start from the top.
Security Affairs
JANUARY 20, 2020
Citrix addressed the actively exploited CVE-2019-19781 flaw in Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances. Citrix has released security patches to address actively exploited CVE-2019-19781 vulnerability in Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

WIRED Threat Level
JANUARY 20, 2020
IoT is a security hellscape. One cryptography has a plan to make it a little bit less so.

Reltio
JANUARY 20, 2020
Martin Treder is a master data management expert, speaker and author with more than 15 years of executive level experience working with data and analytics. He has headed up international teams in the world’s largest logistics companies including FedEx, TNT and DHL and is an expert at solving their business problems. His new book on the topic of data and its commercial explains how to prepare and launch the introduction of a data office in your company.

CILIP
JANUARY 20, 2020
CILIP?s third Chinese accreditation at Nanjing University of Information Science and Technology (NUIST). The information management and information systems undergraduate programme from the School of Management Science and Engineering at Nanjing University of Information Science and Technology in East China has been accredited by CILIP. The Bachelor of Science programme in Information Management & Information Systems is a welcome addition to CILIP?
Let's personalize your content