Security Experts Sound Alarm on Zero-Day in Widely Used Log4j Tool
Dark Reading
DECEMBER 10, 2021
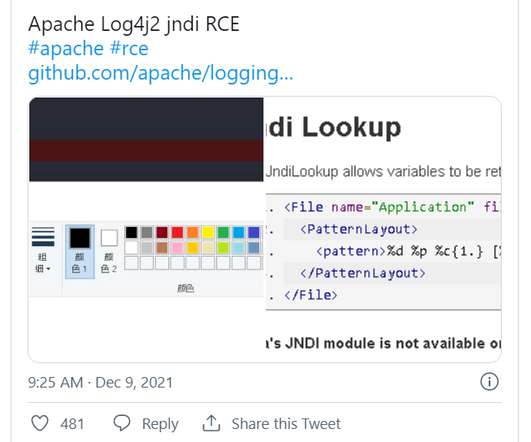
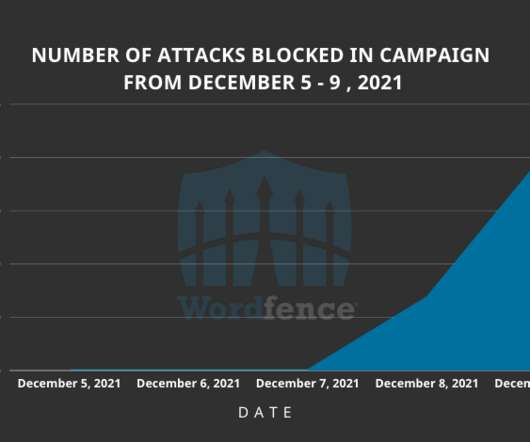
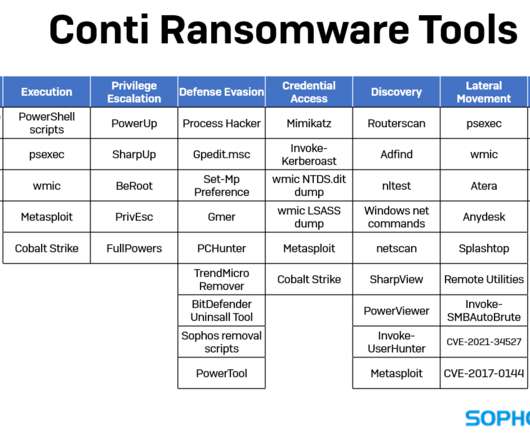
A remote code execution vulnerability in Log4j presents a bigger threat to organizations than even the infamous 2017 Apache Struts vulnerability that felled Equifax, they say.

































Let's personalize your content