Vendor Impersonation Competing with CEO Fraud
KnowBe4
JUNE 23, 2022
Researchers at Abnormal Security have observed an increase in vendor impersonation in business email compromise (BEC) attacks.

KnowBe4
JUNE 23, 2022
Researchers at Abnormal Security have observed an increase in vendor impersonation in business email compromise (BEC) attacks.

Data Breach Today
JUNE 23, 2022
Ping Ventures Will Support Startups Building the Next Generation of Identity Tools Ping Identity is making a $50 million bet it can integrate cutting-edge technology into its own stack through a new in-house corporate venture fund to support identity and access management technology startups. "We want to have a nice overall corporate strategy portfolio," says Ping's Anton Papp.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 23, 2022
The U.S. Securities and Exchange Commission (SEC) is taking steps to crack down on insufficient cyber risk reporting. Related : Making third-party risk audits actionable. Seeking to minimize cybersecurity threat effects, the SEC has proposed several amendments requiring organizations to report on cyber risk in a “fast, comparable, and decision-useful manner.”.

Data Breach Today
JUNE 23, 2022
Vulnerabilities Contained in Certain Hillrom Medical Electrocardiographs A popular line of portable electrocardiographs contains vulnerabilities that allow hackers to execute commands and access sensitive information, federal authorities warn. Device manufacturer Hillrom Medical has released a patch and coordinated disclosure with CISA.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Jamf
JUNE 23, 2022
A new nonprofit organization birthed from the thriving Slack community is working to enhance access and development for IT professionals working with Apple devices.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Matters
JUNE 23, 2022
Kentucky and Maryland recently continued the trend of state insurance departments adopting some version of the National Association of Insurance Commissioners’ (“NAIC”) Insurance Data Security Model Law. Kentucky Governor Andy Beshear signed House Bill 474 into law, and Maryland Governor Larry Hogan signed SB 207. Like the Model Law on which both are based, the laws require licensees of their states to, among other things, maintain a comprehensive written information security program, perform a
Data Breach Today
JUNE 23, 2022
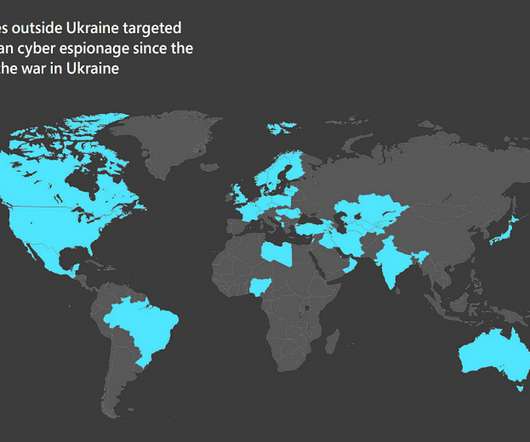
Data Wipers And Phishing Are Weapons In the Kremlin's War A report from the company behind the world's most ubiquitous operating system depicts active cyber scrimmage between Russia and Ukraine and Russia and a slew of other countries. Fighting it is the work of private-public collaboration, Microsoft President Brad Smith writes.

IT Governance
JUNE 23, 2022
The delivery service company Yodel has suffered a “cyber incident” resulting in widespread disruption. Customers awaiting deliveries noted that Yodel’s systems went offline last weekend, and that they have been unable to receive updates since then. In an message posted on its website , Yodel said: “We are working to restore our operations as quickly as possible but for now, order tracking remains unavailable and parcels may arrive later than expected.”.

Data Breach Today
JUNE 23, 2022
The latest edition of the ISMG Security Report investigates the reboot of ransomware group Conti, which supports Russia's invasion of Ukraine. It also discusses why paying ransomware actors is a "business decision" and how to respond to the talent shortage in the financial sector.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

KnowBe4
JUNE 23, 2022
Technology is everywhere in society these days from our communication, shopping, and commerce capabilities. Whether email, online purchases, or using the blockchain, it amounts to large amounts of data collected about people. All this data, while easy to store, is also harder to manage and protect. Users exhibit a variety of behaviors when interacting with this data, and technology tracks those behaviors to effectively identify a specific person based on geography, time, and frequency.

IT Governance
JUNE 23, 2022
This week, we discuss a cyber attack that’s disrupted Yodel’s deliveries, new tactics from a ransomware gang, the government’s plans for reforming UK data privacy law, and the importance of a defence-in-depth approach to cyber security. The post IT Governance Podcast Episode 2: Yodel, ransomware, the Data Reform Bill and cyber defence in depth appeared first on IT Governance UK Blog.

KnowBe4
JUNE 23, 2022
Amazon Prime Days this year are July 12 - 13th 2022. As a result, cybercriminals are taking every step to capitalize on the holiday with new phishing attacks. I have been getting asked about common types of Amazon-related scams and wanted to share what to look out for.

Dark Reading
JUNE 23, 2022
Malicious invoices coming from the accounting software's legitimate domain are used to harvest phone numbers and carry out fraudulent credit-card transactions.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Hunton Privacy
JUNE 23, 2022
On May 29, 2022, the Maryland legislature enacted House Bill 962 , which amends Maryland’s Personal Information Protection Act (the “Act”). The amendments update and clarify various aspects of the Act, including, but not limited to, the timeframe for reporting a data breach affected individuals, and content requirements for providing notice to the Maryland Attorney General.

KnowBe4
JUNE 23, 2022
Rather than run a complex credential harvesting phishing scam, attackers use existing information about their victim and hijack a popular web service account *before* it’s created.

Schneier on Security
JUNE 23, 2022
Nadiya Kostyuk and Susan Landau wrote an interesting paper: “ Dueling Over DUAL_EC_DRBG: The Consequences of Corrupting a Cryptographic Standardization Process “: Abstract: In recent decades, the U.S. National Institute of Standards and Technology (NIST), which develops cryptographic standards for non-national security agencies of the U.S. government, has emerged as the de facto international source for cryptographic standards.
Security Affairs
JUNE 23, 2022
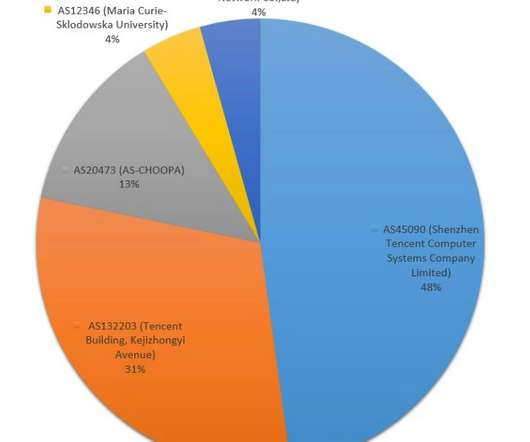
China-linked APT group Tropic Trooper has been spotted previously undocumented malware written in Nim language. Check Point Research uncovered an activity cluster with ties to China-linked APT Tropic Trooper (aka Earth Centaur, KeyBoy, and Pirate Panda) which involved the use of a previously undescribed loader (dubbed “Nimbda”) written in Nim language.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

KnowBe4
JUNE 23, 2022
Lawsuits over denied cyber insurance claims provide insight into what you should and shouldn’t expect from your policy – and that actions by your own users may make the difference.

Jamf
JUNE 23, 2022
Jamf solutions received top marks again in this season’s G2 report, with endpoint protection solution Jamf Protect taking its place in the spotlight.

KnowBe4
JUNE 23, 2022
The free and unmonitored webpage publishing platform has been identified as being used in phishing scams dating back as early as mid-2019, as a key part to bypass security solutions.

Dark Reading
JUNE 23, 2022
The credential-phishing attack leverages social engineering and brand impersonation techniques to lead users to a spoofed MetaMask verification page.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Security Affairs
JUNE 23, 2022
Taiwanese company QNAP is addressing a critical PHP vulnerability that could be exploited to achieve remote code execution. Taiwanese vendor QNAP is addressing a critical PHP vulnerability, tracked as CVE-2019-11043 (CVSS score 9.8 out of 10), that could be exploited to achieve remote code execution. In certain configurations of FPM setup it is possible to trigger a buffer overflaw related to the memory space reserved for FCGI protocol data, potentially leading to the remote code execution.

Dark Reading
JUNE 23, 2022
Bronze Starlight’s use of multiple ransomware families and its victim-targeting suggest there’s more to the group’s activities than just financial gain, security vendor says.

WIRED Threat Level
JUNE 23, 2022
The spyware has been used to target people in Italy, Kazakhstan, and Syria, researchers at Google and Lookout have found.
Dark Reading
JUNE 23, 2022
Bipartisan legislation allows cybersecurity experts to work across multiple agencies and provides federal support for local governments.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Security Affairs
JUNE 23, 2022
Researchers at ETH Zurich discovered several critical flaws in the MEGA cloud storage service that could have allowed the decryption of user data. MEGA has addressed multiple vulnerabilities in its cloud storage service that could have allowed threat actors to decrypt user data stored in encrypted form. Data on Mega services is end-to-end encrypted client-side using the AES algorithm, this means that the company does not know the encryption keys to uploaded files and cannot view the content.

Dark Reading
JUNE 23, 2022
ShiftLeft's Manish Gupta join Dark Reading's Terry Sweeney at Dark Reading News Desk during RSA Conference to talk about looking at vulnerability management through the lens of "attackability.

WIRED Threat Level
JUNE 23, 2022
After months of digging into privacy and security issues around these apps, I have some serious concerns.
Let's personalize your content